Ransomware attacks are one of the fastest-growing cybersecurity threats, with damages exceeding $20 billion annually. These malicious attacks encrypt your data, holding it hostage until you pay a ransom, and they often target both individuals and businesses. The stakes are higher than ever, making it critical to have robust ransomware protection in place.
Acronis anti-ransomware protection has emerged as a leading solution, offering advanced features like real-time threat detection, AI-powered defenses, and automated backups. In this guide, we’ll explore how Acronis can safeguard your data, why it’s a must-have in 2025, and how you can easily download and set it up to protect your digital assets.
What is Ransomware?
Ransomware is a type of malicious software (malware) designed to block access to your data by encrypting it. Attackers then demand a ransom—typically paid in cryptocurrency like Bitcoin—for the decryption key. If the ransom isn’t paid, victims may lose access to their files forever.
Ransomware attacks have evolved dramatically in recent years, becoming more sophisticated, targeted, and damaging. Let’s break down how ransomware works, its impact, and real-world examples to make the concept clear.
How Ransomware Works
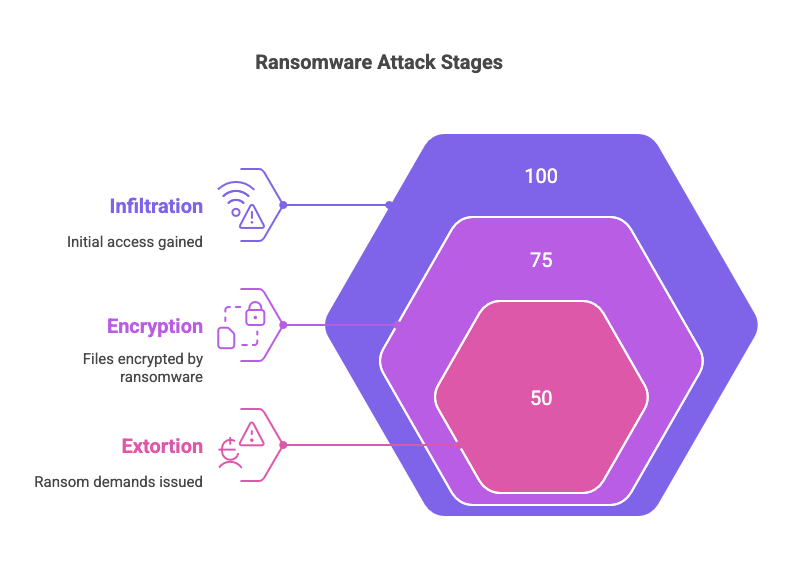
Ransomware operates in three distinct stages:
- Infiltration: Attackers gain access to your device or network through common vulnerabilities, such as:
- Phishing Emails: Cybercriminals craft convincing emails to trick users into clicking malicious links or downloading infected attachments. Phishing scams remain the top entry point for ransomware.
- Unsecured Public Wi-Fi: Many public Wi-Fi networks lack encryption, making them easy targets for hackers to intercept your data. Learn why unsecured Wi-Fi is dangerous.
- Software Vulnerabilities: Outdated software or unpatched systems are another common attack vector. The Verizon Data Breach Investigations Report highlights how unpatched vulnerabilities contribute to ransomware attacks.
- Encryption: Once inside your system, ransomware encrypts files using advanced algorithms. Victims often see a ransom note demanding payment to unlock their data.
- Extortion: Attackers escalate their demands by threatening to:
- Delete encrypted files permanently.
- Publicly leak sensitive information, a tactic known as double extortion.
Real-World Example: The WannaCry Attack
One of the most infamous ransomware attacks, WannaCry, struck in 2017. It infected over 230,000 systems across 150 countries by exploiting a vulnerability in Microsoft’s software. Victims were presented with ransom demands ranging from $300 to $600 in Bitcoin. This attack caused widespread disruptions to hospitals, banks, and government systems, demonstrating how devastating ransomware can be. According to Europol, WannaCry cost global businesses an estimated $4 billion.
The Impact of Ransomware on Businesses and Individuals
Ransomware doesn’t just lock files; it disrupts lives and businesses. Here are some key impacts:
| Impact | Details |
|---|---|
| Financial Losses | The average ransom demand for businesses now exceeds $570,000, and some attacks on larger enterprises have demanded $10 million or more. |
| Reputation Damage | Companies suffering data breaches often experience severe reputational harm, as outlined in IBM’s Data Breach Report. |
| Downtime | Organizations affected by ransomware experience an average downtime of 21 days, causing lost productivity and revenue. |
| Legal Consequences | Failing to secure sensitive data can result in fines under regulations like GDPR, especially if stolen data involves personal or financial information. |
Types of Ransomware
Understanding the different types of ransomware helps clarify why they’re so dangerous. Below are the most common types:
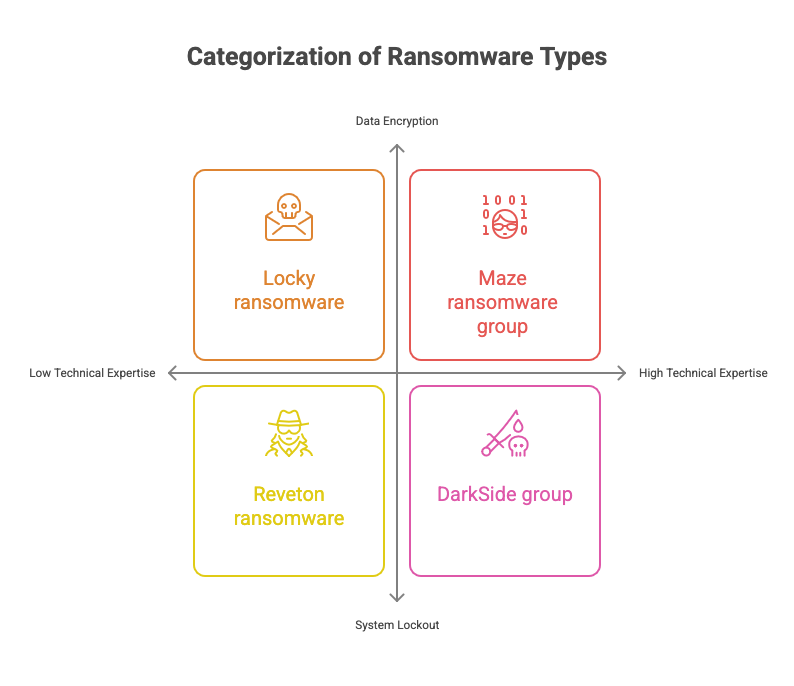
- Crypto Ransomware:
- How It Works: Encrypts files and demands payment for the decryption key.
- Example: The Locky ransomware, which spreads through phishing emails, encrypted files for thousands of victims in 2016.
- Locker Ransomware:
- How It Works: Locks users out of their entire system, rendering it unusable until payment is made.
- Example: Reveton ransomware pretended to be law enforcement, threatening users with fines unless they paid a ransom.
- Double Extortion Ransomware:
- How It Works: Encrypts data while threatening to release sensitive information unless payment is made.
- Example: The Maze ransomware group pioneered double extortion tactics, stealing data and leaking it online.
- Ransomware-as-a-Service (RaaS):
- How It Works: Criminals purchase pre-built ransomware from developers and launch attacks with little technical expertise.
- Example: The DarkSide group, which targeted Colonial Pipeline in 2021, disrupted the fuel supply chain on the U.S. East Coast.
Ransomware Trends: A Look at the Data
The growing scale and sophistication of ransomware attacks highlight the urgent need for protection. Below is a chart visualizing ransomware costs over the years:
Ransomware Damage Costs Worldwide (2016–2025)
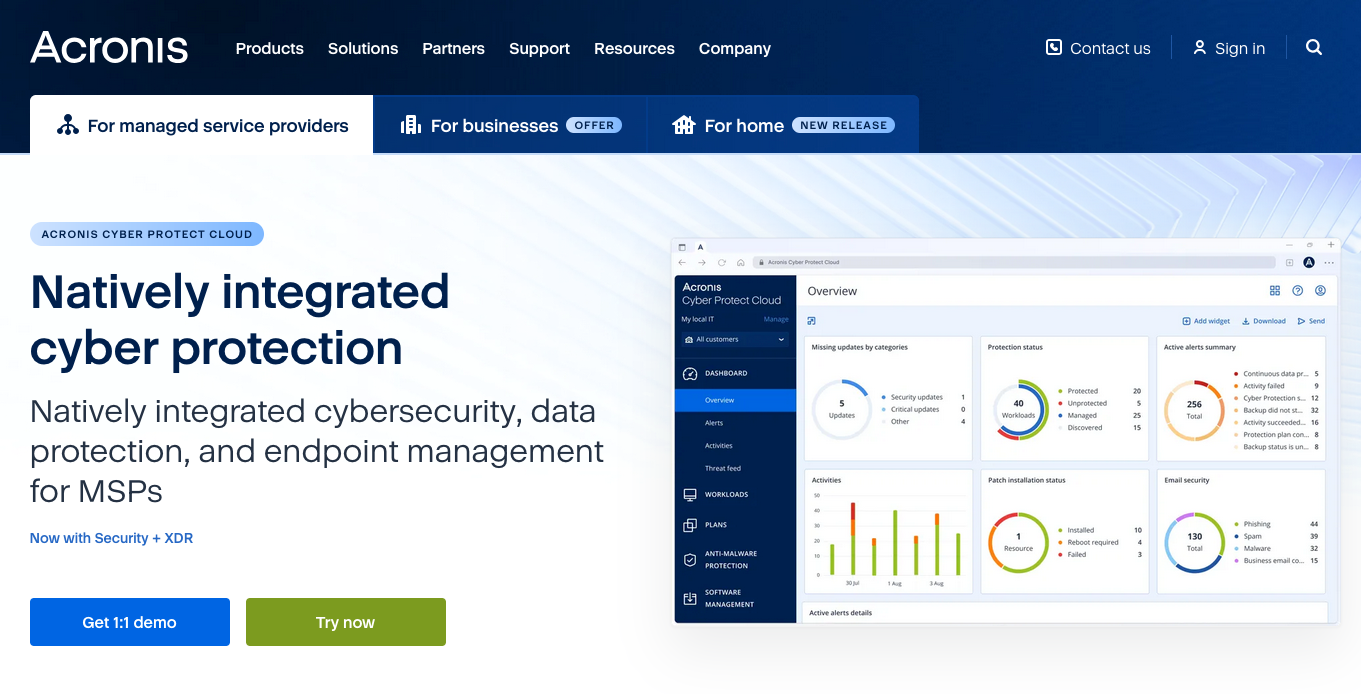
Why Choose Acronis Ransomware Protection?
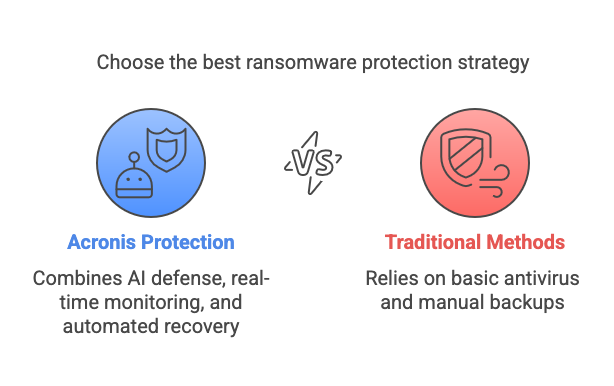
With ransomware attacks becoming more sophisticated every year, relying on basic antivirus software or traditional backups is no longer enough. Acronis ransomware protection offers a cutting-edge solution by combining AI-driven malware defense, real-time monitoring, and automated backup and recovery into a single, powerful platform.
Acronis can restore affected files that have been encrypted or damaged by ransomware, ensuring users can quickly retrieve clean versions after a security breach.
Here’s what makes Acronis unique, the key features it provides, and why it’s a must-have for individuals and businesses alike.
What Makes Acronis Ransomware Protection Unique?
Acronis stands out because it doesn’t just protect your files—it provides a proactive and reactive anti-ransomware approach to ransomware. While many tools focus solely on detection, Acronis pairs it with automated data recovery, ensuring minimal disruption even if an attack occurs.
Unlike traditional antivirus software that often struggles with advanced threats, Acronis leverages AI-based algorithms to identify suspicious behavior before it can damage your system. This proactive approach places it among the most advanced cybersecurity solutions available (see Acronis’ official features).
Key Features of Acronis Ransomware Protection
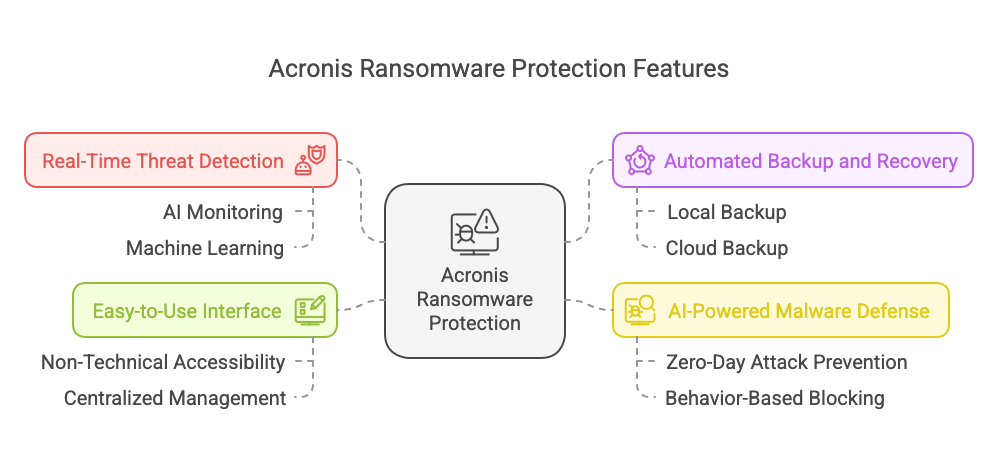
Real-Time Threat Detection
Acronis actively monitors your system for unusual behavior, such as unauthorized file encryption or unexpected software activity. This feature is powered by AI and machine learning, which allows it to stay ahead of evolving ransomware tactics. According to Statista, machine learning-powered cybersecurity tools reduce false positives by up to 30%, making Acronis both efficient and reliable.
Automated Backup and Recovery
Ransomware often locks you out of your data, but with Acronis’ dual backup system, your files remain safe. Backups are stored both locally and in the cloud, so even if your system is compromised, you can restore your data in minutes. This ensures zero downtime, a critical factor for businesses where every second matters (learn more about cloud backup benefits).
AI-Powered Malware Defense
Traditional antivirus solutions rely on databases of known threats, but Acronis uses behavior-based detection. This means it can block zero-day ransomware attacks—new and emerging threats that haven’t yet been cataloged. In 2022 alone, zero-day attacks accounted for over 50% of successful breaches (source).
Easy-to-Use Interface
Acronis is designed with simplicity in mind, making it accessible even for non-technical users. From setting up automated backups to enabling real-time monitoring, every step is intuitive. For businesses, Acronis also offers centralized management tools to monitor multiple devices through a single dashboard.
Benefits of Using Acronis for Ransomware Protection
| Feature | Benefit |
|---|---|
| Proactive Threat Blocking | Prevents ransomware from encrypting files by detecting threats in real-time. |
| Quick Data Recovery | Restores encrypted or deleted files in minutes, reducing downtime significantly. |
| Cloud Integration | Safeguards backups in the cloud, ensuring data is always accessible—even in the event of hardware damage. |
| Cost-Effective | Avoids ransom payments, which can range from thousands to millions of dollars. |
Real-World Success Story: Protecting a Healthcare Provider
A healthcare provider in Europe implemented Acronis ransomware protection after suffering a ransomware attack that encrypted patient records. Within seconds, Acronis detected and stopped the attack, preventing further encryption. Using its backup and recovery system, the provider restored all files within four hours, avoiding a ransom payment of $350,000. Read the full case study here.
Acronis vs. Competitors: Why It’s the Best Choice
While other tools like Norton 360 and Bitdefender offer solid antivirus features, Acronis’ combination of ransomware-specific protection and integrated backup solutions gives it an edge.
| Feature | Acronis | Norton 360 | Bitdefender |
|---|---|---|---|
| AI-Powered Detection | Yes | Yes | Yes |
| Automated Backups | Yes | No | Limited |
| Cloud Backup Integration | Yes | Yes | Yes |
| Zero-Day Threat Defense | Yes | Yes | Yes |
| Ransomware-Specific Features | Yes | Limited | Limited |
This comparison makes it clear: Acronis isn’t just an antivirus—it’s a complete cyber resilience solution.
Why Businesses Trust Acronis
According to Cybersecurity Ventures, ransomware attacks occur every 11 seconds, making advanced protection more critical than ever. Businesses worldwide, including Fortune 500 companies, rely on Acronis to ensure their data is secure.
“Acronis is a game-changer for cybersecurity. Its AI-powered ransomware protection saved our operations when no other tool could.” – Michael L., IT Director
How to Download and Set Up Acronis Ransomware Protection
Setting up Acronis ransomware protection is quick and straightforward, making it accessible for individuals and businesses alike. In this section, we’ll walk you through the process of downloading, installing, and configuring the software for optimal protection.
Step 1: Visit the Official Acronis Website
To ensure you download the authentic software, start by visiting the official Acronis website. Avoid third-party websites, as these may host outdated or potentially tampered versions of the software.
- Tip: Bookmark the official Acronis page for easy access to updates and support resources.
Step 2: Choose the Right Plan for Your Needs
Acronis offers several plans tailored to different user requirements. Here’s an overview to help you decide:
| Plan | Features | Best For |
|---|---|---|
| Acronis Cyber Protect Home Office | Includes ransomware protection, automated backups, and cloud integration. | Individuals and families. |
| Acronis Cyber Protect Standard | Advanced AI-powered threat detection, backup recovery, and centralized management tools. | Small businesses with basic needs. |
| Acronis Cyber Protect Advanced | Comprehensive protection with additional features like forensic backup and remote device management. | Enterprises and IT professionals. |
Once you’ve identified the right plan, click “Buy Now” or select the free trial option for first-time users.
- Tip: New users can explore a free 30-day trial to test the software’s features before committing to a paid plan.
Step 3: Download and Install the Software
- After selecting your plan, click the “Download” button on the Acronis website.
- Locate the downloaded file (e.g., AcronisSetup.exe or AcronisInstaller.dmg) and double-click it to begin the installation process.
- Follow the on-screen instructions to complete the setup.
- Tip: During installation, opt into automatic updates to ensure you’re always protected against the latest ransomware threats.
Step 4: Configure Settings for Optimal Protection
Once installed, Acronis ransomware protection offers several customization options to maximize your security:
Enable Real-Time Monitoring
- Turn on Active Protection, which scans your system in real-time for suspicious behavior, such as unauthorized encryption of files.
Set Up Automatic Backups
- Go to the Backup Settings tab.
- Choose the frequency of backups (e.g., daily, weekly).
- Select your preferred storage option:
- Local Storage: Backup files directly to your computer or external drives.
- Cloud Storage: Store data securely in the Acronis Cloud, ensuring access even if your hardware is compromised.
Adjust Advanced Security Features
- Enable anti-cryptojacking protection, which prevents unauthorized use of your system’s resources for cryptocurrency mining.
- Activate web filtering to block malicious websites linked to phishing or ransomware attacks.
Example: Backup Strategy for a Small Business
A marketing agency with 15 employees uses Acronis to schedule daily cloud backups for its client databases and creative files. In the event of a ransomware attack, the agency can restore its most recent backup within minutes, avoiding any downtime.
Step 5: Test the Software
To ensure everything is working properly:
- Run a security scan from the Acronis dashboard.
- Perform a test backup to verify your files are being stored correctly.
- Simulate a ransomware attack using a safe testing tool, like the Acronis Active Protection Test File, which mimics how ransomware behaves. This helps confirm that the software can detect and block threats effectively.
Step 6: Stay Updated and Renew Your Plan
- Automatic Updates: Acronis automatically updates its ransomware definitions and features, so there’s no need to manually download new versions.
- Renewal Reminders: Set a reminder to renew your subscription on time to avoid lapses in protection.
Why Ease of Setup Matters
According to a report by Gartner, ease of use is one of the top factors businesses consider when choosing cybersecurity software. Acronis’ intuitive setup process ensures that even non-technical users can implement robust ransomware protection with minimal effort.
Here’s the next section: Case Studies and Testimonials. This section provides real-world examples and feedback to build trust and demonstrate Acronis’ effectiveness.
Case Studies and Testimonials: Why Businesses Trust Acronis Ransomware Protection
When choosing cybersecurity software, real-world results matter. Acronis ransomware protection has proven its value across industries, helping businesses avoid costly downtime, data loss, and ransom payments. Below, we highlight two compelling case studies and share customer testimonials that illustrate why Acronis is a trusted name in ransomware protection.
How Acronis Saved a Healthcare Provider from a Devastating Ransomware Attack
The Challenge:
In 2022, a European healthcare provider fell victim to a ransomware attack that encrypted critical patient records, including medical histories and treatment plans. The attackers demanded a ransom of $350,000 to restore access.
The Acronis Solution:
Fortunately, the provider had implemented Acronis ransomware protection across its network. Here’s how Acronis prevented a disaster:
- Real-Time Detection: Acronis detected the ransomware as soon as it attempted to encrypt files, halting the attack before further damage could occur.
- Automated Backups: Using the provider’s most recent cloud backup, Acronis restored all patient data within four hours—avoiding ransom payment and ensuring continuity of care.
- Proactive Protection: Post-attack, Acronis strengthened the organization’s defenses by updating their system configurations and implementing stricter access controls.
Results:
- Downtime Reduced: Full operations were restored in just 4 hours.
- Ransom Payment Avoided: The $350,000 demand was bypassed entirely.
- Data Integrity Maintained: No patient records were lost or leaked.
E-commerce Business: Resilience in the Face of a Ransomware Threat
The Challenge:
A mid-sized online retailer in the United States experienced a ransomware attack during the busy holiday shopping season. The attack encrypted their entire product database, leaving the company unable to process orders.
The Acronis Solution:
The business had recently adopted Acronis Cyber Protect, which included ransomware protection and automated cloud backups. Here’s what happened:
- Behavior-Based Detection: Acronis flagged unusual encryption activity and stopped the ransomware before it could spread.
- Instant Recovery: The business used Acronis’ incremental backup system to restore their product database in under 90 minutes.
- Zero Downtime: By leveraging cloud backups, the company avoided significant disruptions to their operations.
Results:
- 90 Minutes to Recovery: The business resumed full operations within hours of the attack.
- Zero Revenue Loss: Despite the timing of the attack, sales remained unaffected.
- Customer Trust Preserved: Proactive communication and swift resolution kept customer satisfaction high.
Customer Testimonials
What Businesses Are Saying About Acronis
“We owe our business continuity to Acronis. Their ransomware protection and automated backups stopped an attack in its tracks and allowed us to recover everything without paying a cent.”
— Michael R., IT Manager, Financial Services Firm
“Acronis is incredibly easy to use, even for non-technical staff. The cloud backups are seamless, and the ransomware protection is second to none. We highly recommend it for small businesses.”
— Susan K., Owner, Marketing Agency
“The AI-powered detection is a game-changer. Acronis identified and blocked a ransomware attempt that other tools missed. I sleep better knowing our systems are safe.”
— John D., CTO, E-commerce Brand
Why Testimonials and Case Studies Matter
According to a BrightLocal consumer review survey, 92% of consumers trust testimonials and case studies as much as personal recommendations. Highlighting real-world success stories helps demonstrate the tangible benefits of Acronis ransomware protection.
FAQs About Acronis Ransomware Protection
To ensure you have all the information you need about Acronis ransomware protection, we’ve compiled answers to the most frequently asked questions. These insights will help you understand how the software works, its features, and how it can safeguard your data.
Is Acronis ransomware protection easy to use?
Yes, Acronis is designed to be intuitive and user-friendly. Its clean interface allows both individuals and IT professionals to easily set up backups, monitor ransomware threats, and configure security settings. For businesses managing multiple devices, Acronis provides a centralized management dashboard, streamlining administration across teams.
Can Acronis protect against zero-day attacks?
Absolutely. Unlike traditional antivirus software that relies on known malware signatures, Acronis uses AI-powered behavior detection to block zero-day attacks—new, previously unidentified ransomware strains. According to CrowdStrike’s Global Threat Report, zero-day threats accounted for over 50% of successful breaches in 2022, making Acronis’ proactive approach essential.
How much does Acronis ransomware protection cost?
Acronis offers flexible pricing plans tailored to different user needs:
- Home Office Plans: Starting at $49.99/year for individuals.
- Business Plans: Pricing varies depending on the number of devices and advanced features. Visit the Acronis pricing page for the most accurate and up-to-date pricing.
Is there a free trial or demo available?
Yes, Acronis provides a 30-day free trial that allows you to explore all the core features of its ransomware protection software. This trial includes access to backup and recovery tools, real-time monitoring, and cloud storage. Sign up for the free trial here.
What makes Acronis different from traditional antivirus software?
While antivirus programs focus on detecting and removing known malware, Acronis ransomware protection offers a more comprehensive approach:
- Real-Time Monitoring: Constantly scans for unusual activity like unauthorized encryption.
- Backup Integration: Provides automated backups and cloud storage to ensure your data is recoverable.
- AI-Powered Detection: Blocks zero-day attacks and evolving ransomware strains. These features make Acronis an all-in-one solution for ransomware resilience.
Does Acronis work for businesses of all sizes?
Yes, Acronis offers solutions for small businesses, medium-sized enterprises, and large corporations. Features like centralized management, forensic backup, and advanced ransomware defense make it scalable for teams of all sizes.
Can Acronis protect my cloud data?
Yes, Acronis integrates seamlessly with cloud platforms, offering robust cloud backup and recovery options. This ensures your data is protected against ransomware, hardware failures, and other risks, even if it’s stored off-site.
How does Acronis handle double extortion ransomware?
Double extortion ransomware is particularly dangerous, as attackers threaten to leak stolen data. Acronis defends against these attacks by:
- Blocking the Attack: Using AI and real-time monitoring to detect and stop ransomware before it encrypts your files.
- Encrypting Backups: Ensuring that even if sensitive data is leaked, the backups remain secure and inaccessible to attackers.
Is Acronis ransomware protection resource-intensive?
No, Acronis is optimized for performance and runs in the background without slowing down your system. Its efficient design ensures minimal resource usage, even when performing intensive tasks like full-system backups or malware scans.
What support options are available with Acronis?
Acronis offers 24/7 customer support through live chat, email, and phone. Additionally, the Acronis Knowledge Base provides comprehensive guides, FAQs, and troubleshooting resources to help users resolve issues quickly.
Can Acronis protect against ransomware on mobile devices?
Yes, Acronis extends its ransomware protection to mobile devices, offering secure backup and recovery options for Android and iOS. This ensures your personal photos, files, and app data remain safe from mobile-based ransomware threats.
How do Acronis Ransomware Protection Monitors safeguard against malicious code?
Acronis Ransomware Protection Monitors safeguard against malicious code by actively monitoring your system for suspicious activities that could indicate a ransomware attack. This includes detecting and blocking attempts to inject malicious code into your files or system processes. As new strains of ransomware emerge, Acronis updates its protection mechanisms, ensuring it is completely compatible with the latest security threats.
What steps does Acronis Active Protection take to manage accidental deletions?
Acronis Active Protection manages accidental deletions by creating a local cache or temporary files that store the latest file versions. This feature allows users to restore important files that were accidentally deleted, ensuring data integrity and minimizing the impact of potential security incidents. This proactive approach helps preserve important data against unforeseen deletions.
Can suspicious activities affect the performance of my free cloud storage?
Yes, suspicious activities can affect the performance of your free cloud storage by potentially compromising data integrity or leading to unauthorized access. Acronis Active Protection helps monitor and identify such activities, enabling quick responses to threats. Maintaining vigilance against suspicious code ensures that normal activities and data within your cloud storage remain secure.
How does Acronis ensure compatibility with the latest file versions and security standards?
Acronis ensures compatibility with the latest file versions and security standards by continuously updating its software to address new ransomware strains and evolving threats. The integration of features such as Acronis Active Protection allows the system to adapt and remain effective against both existing and new security challenges, providing robust protection for users’ data.

Ransomware attacks are one of the fastest-growing cybersecurity threats, with damages exceeding $20 billion annually. These malicious attacks encrypt your data, holding it hostage until you pay a ransom, and they often target both individuals and businesses. The stakes are higher than ever, making it critical to have robust ransomware protection in place.
Acronis anti-ransomware protection has emerged as a leading solution, offering advanced features like real-time threat detection, AI-powered defenses, and automated backups. In this guide, we’ll explore how Acronis can safeguard your data, why it’s a must-have in 2025, and how you can easily download and set it up to protect your digital assets.
What is Ransomware?
Ransomware is a type of malicious software (malware) designed to block access to your data by encrypting it. Attackers then demand a ransom—typically paid in cryptocurrency like Bitcoin—for the decryption key. If the ransom isn’t paid, victims may lose access to their files forever.
Ransomware attacks have evolved dramatically in recent years, becoming more sophisticated, targeted, and damaging. Let’s break down how ransomware works, its impact, and real-world examples to make the concept clear.
How Ransomware Works
Ransomware operates in three distinct stages:
- Infiltration: Attackers gain access to your device or network through common vulnerabilities, such as:
- Phishing Emails: Cybercriminals craft convincing emails to trick users into clicking malicious links or downloading infected attachments. Phishing scams remain the top entry point for ransomware.
- Unsecured Public Wi-Fi: Many public Wi-Fi networks lack encryption, making them easy targets for hackers to intercept your data. Learn why unsecured Wi-Fi is dangerous.
- Software Vulnerabilities: Outdated software or unpatched systems are another common attack vector. The Verizon Data Breach Investigations Report highlights how unpatched vulnerabilities contribute to ransomware attacks.
- Encryption: Once inside your system, ransomware encrypts files using advanced algorithms. Victims often see a ransom note demanding payment to unlock their data.
- Extortion: Attackers escalate their demands by threatening to:
- Delete encrypted files permanently.
- Publicly leak sensitive information, a tactic known as double extortion.
Real-World Example: The WannaCry Attack
One of the most infamous ransomware attacks, WannaCry, struck in 2017. It infected over 230,000 systems across 150 countries by exploiting a vulnerability in Microsoft’s software. Victims were presented with ransom demands ranging from $300 to $600 in Bitcoin. This attack caused widespread disruptions to hospitals, banks, and government systems, demonstrating how devastating ransomware can be. According to Europol, WannaCry cost global businesses an estimated $4 billion.
The Impact of Ransomware on Businesses and Individuals
Ransomware doesn’t just lock files; it disrupts lives and businesses. Here are some key impacts:
| Impact | Details |
|---|---|
| Financial Losses | The average ransom demand for businesses now exceeds $570,000, and some attacks on larger enterprises have demanded $10 million or more. |
| Reputation Damage | Companies suffering data breaches often experience severe reputational harm, as outlined in IBM’s Data Breach Report. |
| Downtime | Organizations affected by ransomware experience an average downtime of 21 days, causing lost productivity and revenue. |
| Legal Consequences | Failing to secure sensitive data can result in fines under regulations like GDPR, especially if stolen data involves personal or financial information. |
Types of Ransomware
Understanding the different types of ransomware helps clarify why they’re so dangerous. Below are the most common types:
- Crypto Ransomware:
- How It Works: Encrypts files and demands payment for the decryption key.
- Example: The Locky ransomware, which spreads through phishing emails, encrypted files for thousands of victims in 2016.
- Locker Ransomware:
- How It Works: Locks users out of their entire system, rendering it unusable until payment is made.
- Example: Reveton ransomware pretended to be law enforcement, threatening users with fines unless they paid a ransom.
- Double Extortion Ransomware:
- How It Works: Encrypts data while threatening to release sensitive information unless payment is made.
- Example: The Maze ransomware group pioneered double extortion tactics, stealing data and leaking it online.
- Ransomware-as-a-Service (RaaS):
- How It Works: Criminals purchase pre-built ransomware from developers and launch attacks with little technical expertise.
- Example: The DarkSide group, which targeted Colonial Pipeline in 2021, disrupted the fuel supply chain on the U.S. East Coast.
Ransomware Trends: A Look at the Data
The growing scale and sophistication of ransomware attacks highlight the urgent need for protection. Below is a chart visualizing ransomware costs over the years:
Ransomware Damage Costs Worldwide (2016–2025)
Why Choose Acronis Ransomware Protection?
With ransomware attacks becoming more sophisticated every year, relying on basic antivirus software or traditional backups is no longer enough. Acronis ransomware protection offers a cutting-edge solution by combining AI-driven malware defense, real-time monitoring, and automated backup and recovery into a single, powerful platform.
Acronis can restore affected files that have been encrypted or damaged by ransomware, ensuring users can quickly retrieve clean versions after a security breach.
Here’s what makes Acronis unique, the key features it provides, and why it’s a must-have for individuals and businesses alike.
What Makes Acronis Ransomware Protection Unique?
Acronis stands out because it doesn’t just protect your files—it provides a proactive and reactive anti-ransomware approach to ransomware. While many tools focus solely on detection, Acronis pairs it with automated data recovery, ensuring minimal disruption even if an attack occurs.
Unlike traditional antivirus software that often struggles with advanced threats, Acronis leverages AI-based algorithms to identify suspicious behavior before it can damage your system. This proactive approach places it among the most advanced cybersecurity solutions available (see Acronis’ official features).
Key Features of Acronis Ransomware Protection
Real-Time Threat Detection
Acronis actively monitors your system for unusual behavior, such as unauthorized file encryption or unexpected software activity. This feature is powered by AI and machine learning, which allows it to stay ahead of evolving ransomware tactics. According to Statista, machine learning-powered cybersecurity tools reduce false positives by up to 30%, making Acronis both efficient and reliable.
Automated Backup and Recovery
Ransomware often locks you out of your data, but with Acronis’ dual backup system, your files remain safe. Backups are stored both locally and in the cloud, so even if your system is compromised, you can restore your data in minutes. This ensures zero downtime, a critical factor for businesses where every second matters (learn more about cloud backup benefits).
AI-Powered Malware Defense
Traditional antivirus solutions rely on databases of known threats, but Acronis uses behavior-based detection. This means it can block zero-day ransomware attacks—new and emerging threats that haven’t yet been cataloged. In 2022 alone, zero-day attacks accounted for over 50% of successful breaches (source).
Easy-to-Use Interface
Acronis is designed with simplicity in mind, making it accessible even for non-technical users. From setting up automated backups to enabling real-time monitoring, every step is intuitive. For businesses, Acronis also offers centralized management tools to monitor multiple devices through a single dashboard.
Benefits of Using Acronis for Ransomware Protection
| Feature | Benefit |
|---|---|
| Proactive Threat Blocking | Prevents ransomware from encrypting files by detecting threats in real-time. |
| Quick Data Recovery | Restores encrypted or deleted files in minutes, reducing downtime significantly. |
| Cloud Integration | Safeguards backups in the cloud, ensuring data is always accessible—even in the event of hardware damage. |
| Cost-Effective | Avoids ransom payments, which can range from thousands to millions of dollars. |
Real-World Success Story: Protecting a Healthcare Provider
A healthcare provider in Europe implemented Acronis ransomware protection after suffering a ransomware attack that encrypted patient records. Within seconds, Acronis detected and stopped the attack, preventing further encryption. Using its backup and recovery system, the provider restored all files within four hours, avoiding a ransom payment of $350,000. Read the full case study here.
Acronis vs. Competitors: Why It’s the Best Choice
While other tools like Norton 360 and Bitdefender offer solid antivirus features, Acronis’ combination of ransomware-specific protection and integrated backup solutions gives it an edge.
| Feature | Acronis | Norton 360 | Bitdefender |
|---|---|---|---|
| AI-Powered Detection | Yes | Yes | Yes |
| Automated Backups | Yes | No | Limited |
| Cloud Backup Integration | Yes | Yes | Yes |
| Zero-Day Threat Defense | Yes | Yes | Yes |
| Ransomware-Specific Features | Yes | Limited | Limited |
This comparison makes it clear: Acronis isn’t just an antivirus—it’s a complete cyber resilience solution.
Why Businesses Trust Acronis
According to Cybersecurity Ventures, ransomware attacks occur every 11 seconds, making advanced protection more critical than ever. Businesses worldwide, including Fortune 500 companies, rely on Acronis to ensure their data is secure.
“Acronis is a game-changer for cybersecurity. Its AI-powered ransomware protection saved our operations when no other tool could.” – Michael L., IT Director
How to Download and Set Up Acronis Ransomware Protection
Setting up Acronis ransomware protection is quick and straightforward, making it accessible for individuals and businesses alike. In this section, we’ll walk you through the process of downloading, installing, and configuring the software for optimal protection.
Step 1: Visit the Official Acronis Website
To ensure you download the authentic software, start by visiting the official Acronis website. Avoid third-party websites, as these may host outdated or potentially tampered versions of the software.
- Tip: Bookmark the official Acronis page for easy access to updates and support resources.
Step 2: Choose the Right Plan for Your Needs
Acronis offers several plans tailored to different user requirements. Here’s an overview to help you decide:
| Plan | Features | Best For |
|---|---|---|
| Acronis Cyber Protect Home Office | Includes ransomware protection, automated backups, and cloud integration. | Individuals and families. |
| Acronis Cyber Protect Standard | Advanced AI-powered threat detection, backup recovery, and centralized management tools. | Small businesses with basic needs. |
| Acronis Cyber Protect Advanced | Comprehensive protection with additional features like forensic backup and remote device management. | Enterprises and IT professionals. |
Once you’ve identified the right plan, click “Buy Now” or select the free trial option for first-time users.
- Tip: New users can explore a free 30-day trial to test the software’s features before committing to a paid plan.
Step 3: Download and Install the Software
- After selecting your plan, click the “Download” button on the Acronis website.
- Locate the downloaded file (e.g., AcronisSetup.exe or AcronisInstaller.dmg) and double-click it to begin the installation process.
- Follow the on-screen instructions to complete the setup.
- Tip: During installation, opt into automatic updates to ensure you’re always protected against the latest ransomware threats.
Step 4: Configure Settings for Optimal Protection
Once installed, Acronis ransomware protection offers several customization options to maximize your security:
Enable Real-Time Monitoring
- Turn on Active Protection, which scans your system in real-time for suspicious behavior, such as unauthorized encryption of files.
Set Up Automatic Backups
- Go to the Backup Settings tab.
- Choose the frequency of backups (e.g., daily, weekly).
- Select your preferred storage option:
- Local Storage: Backup files directly to your computer or external drives.
- Cloud Storage: Store data securely in the Acronis Cloud, ensuring access even if your hardware is compromised.
Adjust Advanced Security Features
- Enable anti-cryptojacking protection, which prevents unauthorized use of your system’s resources for cryptocurrency mining.
- Activate web filtering to block malicious websites linked to phishing or ransomware attacks.
Example: Backup Strategy for a Small Business
A marketing agency with 15 employees uses Acronis to schedule daily cloud backups for its client databases and creative files. In the event of a ransomware attack, the agency can restore its most recent backup within minutes, avoiding any downtime.
Step 5: Test the Software
To ensure everything is working properly:
- Run a security scan from the Acronis dashboard.
- Perform a test backup to verify your files are being stored correctly.
- Simulate a ransomware attack using a safe testing tool, like the Acronis Active Protection Test File, which mimics how ransomware behaves. This helps confirm that the software can detect and block threats effectively.
Step 6: Stay Updated and Renew Your Plan
- Automatic Updates: Acronis automatically updates its ransomware definitions and features, so there’s no need to manually download new versions.
- Renewal Reminders: Set a reminder to renew your subscription on time to avoid lapses in protection.
Why Ease of Setup Matters
According to a report by Gartner, ease of use is one of the top factors businesses consider when choosing cybersecurity software. Acronis’ intuitive setup process ensures that even non-technical users can implement robust ransomware protection with minimal effort.
Here’s the next section: Case Studies and Testimonials. This section provides real-world examples and feedback to build trust and demonstrate Acronis’ effectiveness.
Case Studies and Testimonials: Why Businesses Trust Acronis Ransomware Protection
When choosing cybersecurity software, real-world results matter. Acronis ransomware protection has proven its value across industries, helping businesses avoid costly downtime, data loss, and ransom payments. Below, we highlight two compelling case studies and share customer testimonials that illustrate why Acronis is a trusted name in ransomware protection.
How Acronis Saved a Healthcare Provider from a Devastating Ransomware Attack
The Challenge:
In 2022, a European healthcare provider fell victim to a ransomware attack that encrypted critical patient records, including medical histories and treatment plans. The attackers demanded a ransom of $350,000 to restore access.
The Acronis Solution:
Fortunately, the provider had implemented Acronis ransomware protection across its network. Here’s how Acronis prevented a disaster:
- Real-Time Detection: Acronis detected the ransomware as soon as it attempted to encrypt files, halting the attack before further damage could occur.
- Automated Backups: Using the provider’s most recent cloud backup, Acronis restored all patient data within four hours—avoiding ransom payment and ensuring continuity of care.
- Proactive Protection: Post-attack, Acronis strengthened the organization’s defenses by updating their system configurations and implementing stricter access controls.
Results:
- Downtime Reduced: Full operations were restored in just 4 hours.
- Ransom Payment Avoided: The $350,000 demand was bypassed entirely.
- Data Integrity Maintained: No patient records were lost or leaked.
E-commerce Business: Resilience in the Face of a Ransomware Threat
The Challenge:
A mid-sized online retailer in the United States experienced a ransomware attack during the busy holiday shopping season. The attack encrypted their entire product database, leaving the company unable to process orders.
The Acronis Solution:
The business had recently adopted Acronis Cyber Protect, which included ransomware protection and automated cloud backups. Here’s what happened:
- Behavior-Based Detection: Acronis flagged unusual encryption activity and stopped the ransomware before it could spread.
- Instant Recovery: The business used Acronis’ incremental backup system to restore their product database in under 90 minutes.
- Zero Downtime: By leveraging cloud backups, the company avoided significant disruptions to their operations.
Results:
- 90 Minutes to Recovery: The business resumed full operations within hours of the attack.
- Zero Revenue Loss: Despite the timing of the attack, sales remained unaffected.
- Customer Trust Preserved: Proactive communication and swift resolution kept customer satisfaction high.
Customer Testimonials
What Businesses Are Saying About Acronis
“We owe our business continuity to Acronis. Their ransomware protection and automated backups stopped an attack in its tracks and allowed us to recover everything without paying a cent.”
— Michael R., IT Manager, Financial Services Firm
“Acronis is incredibly easy to use, even for non-technical staff. The cloud backups are seamless, and the ransomware protection is second to none. We highly recommend it for small businesses.”
— Susan K., Owner, Marketing Agency
“The AI-powered detection is a game-changer. Acronis identified and blocked a ransomware attempt that other tools missed. I sleep better knowing our systems are safe.”
— John D., CTO, E-commerce Brand
Why Testimonials and Case Studies Matter
According to a BrightLocal consumer review survey, 92% of consumers trust testimonials and case studies as much as personal recommendations. Highlighting real-world success stories helps demonstrate the tangible benefits of Acronis ransomware protection.
FAQs About Acronis Ransomware Protection
To ensure you have all the information you need about Acronis ransomware protection, we’ve compiled answers to the most frequently asked questions. These insights will help you understand how the software works, its features, and how it can safeguard your data.
Is Acronis ransomware protection easy to use?
Yes, Acronis is designed to be intuitive and user-friendly. Its clean interface allows both individuals and IT professionals to easily set up backups, monitor ransomware threats, and configure security settings. For businesses managing multiple devices, Acronis provides a centralized management dashboard, streamlining administration across teams.
Can Acronis protect against zero-day attacks?
Absolutely. Unlike traditional antivirus software that relies on known malware signatures, Acronis uses AI-powered behavior detection to block zero-day attacks—new, previously unidentified ransomware strains. According to CrowdStrike’s Global Threat Report, zero-day threats accounted for over 50% of successful breaches in 2022, making Acronis’ proactive approach essential.
How much does Acronis ransomware protection cost?
Acronis offers flexible pricing plans tailored to different user needs:
- Home Office Plans: Starting at $49.99/year for individuals.
- Business Plans: Pricing varies depending on the number of devices and advanced features. Visit the Acronis pricing page for the most accurate and up-to-date pricing.
Is there a free trial or demo available?
Yes, Acronis provides a 30-day free trial that allows you to explore all the core features of its ransomware protection software. This trial includes access to backup and recovery tools, real-time monitoring, and cloud storage. Sign up for the free trial here.
What makes Acronis different from traditional antivirus software?
While antivirus programs focus on detecting and removing known malware, Acronis ransomware protection offers a more comprehensive approach:
- Real-Time Monitoring: Constantly scans for unusual activity like unauthorized encryption.
- Backup Integration: Provides automated backups and cloud storage to ensure your data is recoverable.
- AI-Powered Detection: Blocks zero-day attacks and evolving ransomware strains. These features make Acronis an all-in-one solution for ransomware resilience.
Does Acronis work for businesses of all sizes?
Yes, Acronis offers solutions for small businesses, medium-sized enterprises, and large corporations. Features like centralized management, forensic backup, and advanced ransomware defense make it scalable for teams of all sizes.
Can Acronis protect my cloud data?
Yes, Acronis integrates seamlessly with cloud platforms, offering robust cloud backup and recovery options. This ensures your data is protected against ransomware, hardware failures, and other risks, even if it’s stored off-site.
How does Acronis handle double extortion ransomware?
Double extortion ransomware is particularly dangerous, as attackers threaten to leak stolen data. Acronis defends against these attacks by:
- Blocking the Attack: Using AI and real-time monitoring to detect and stop ransomware before it encrypts your files.
- Encrypting Backups: Ensuring that even if sensitive data is leaked, the backups remain secure and inaccessible to attackers.
Is Acronis ransomware protection resource-intensive?
No, Acronis is optimized for performance and runs in the background without slowing down your system. Its efficient design ensures minimal resource usage, even when performing intensive tasks like full-system backups or malware scans.
What support options are available with Acronis?
Acronis offers 24/7 customer support through live chat, email, and phone. Additionally, the Acronis Knowledge Base provides comprehensive guides, FAQs, and troubleshooting resources to help users resolve issues quickly.
Can Acronis protect against ransomware on mobile devices?
Yes, Acronis extends its ransomware protection to mobile devices, offering secure backup and recovery options for Android and iOS. This ensures your personal photos, files, and app data remain safe from mobile-based ransomware threats.
How do Acronis Ransomware Protection Monitors safeguard against malicious code?
Acronis Ransomware Protection Monitors safeguard against malicious code by actively monitoring your system for suspicious activities that could indicate a ransomware attack. This includes detecting and blocking attempts to inject malicious code into your files or system processes. As new strains of ransomware emerge, Acronis updates its protection mechanisms, ensuring it is completely compatible with the latest security threats.
What steps does Acronis Active Protection take to manage accidental deletions?
Acronis Active Protection manages accidental deletions by creating a local cache or temporary files that store the latest file versions. This feature allows users to restore important files that were accidentally deleted, ensuring data integrity and minimizing the impact of potential security incidents. This proactive approach helps preserve important data against unforeseen deletions.
Can suspicious activities affect the performance of my free cloud storage?
Yes, suspicious activities can affect the performance of your free cloud storage by potentially compromising data integrity or leading to unauthorized access. Acronis Active Protection helps monitor and identify such activities, enabling quick responses to threats. Maintaining vigilance against suspicious code ensures that normal activities and data within your cloud storage remain secure.
How does Acronis ensure compatibility with the latest file versions and security standards?
Acronis ensures compatibility with the latest file versions and security standards by continuously updating its software to address new ransomware strains and evolving threats. The integration of features such as Acronis Active Protection allows the system to adapt and remain effective against both existing and new security challenges, providing robust protection for users’ data.