Wireshark is a powerful network protocol analyzer widely regarded as an essential tool in cybersecurity. From incident response to forensic investigations, it empowers cybersecurity professionals to monitor, analyze, and troubleshoot network traffic. In this comprehensive guide, we will delve into how Wireshark is used in cybersecurity, with intermediate to advanced examples, step-by-step configurations, and actionable insights to help you master this indispensable tool.
What is Wireshark?
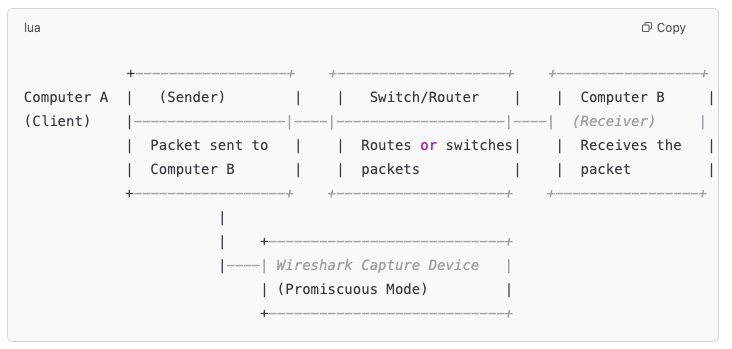
Wireshark captures packets—the basic units of data transmission—traveling across a network. These packets are dissected and presented in a human-readable format for analysis. Wireshark supports thousands of protocols and can be customized for specific use cases, making it an essential component of a cybersecurity professional’s toolkit.
Wireshark operates by placing a network interface into promiscuous mode, capturing all traffic traversing the network. With its advanced filtering, coloring, and dissecting capabilities, Wireshark is ideal for uncovering network anomalies, debugging issues, and investigating potential threats.
Use Cases for Wireshark in Cybersecurity
1. Detecting Man-in-the-Middle (MitM) Attacks
MitM attacks occur when a malicious actor intercepts communications between two parties. These attacks often rely on ARP (Address Resolution Protocol) spoofing to redirect traffic.
How Wireshark Helps:
- Detect anomalous ARP packets, such as duplicate IP addresses assigned to different MAC addresses.
- Identify changes in normal traffic flow, such as unexpected routing through unknown devices.
Configuration Steps:
- Set Filters for ARP Traffic:
- Use the capture filter arp to isolate ARP packets.
- Examine Duplicate Responses:
- Look for repeated Who has and is at messages in the Packet List Pane.
- Visualize Suspicious Patterns:
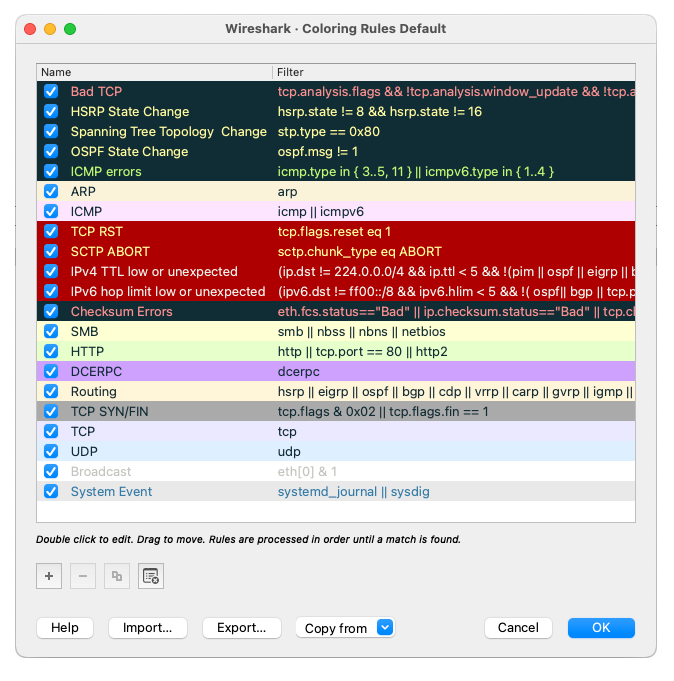
- Customize the coloring rules under View > Coloring Rules to highlight ARP packets from unexpected sources.
Example:
Consider a scenario where Device A and Device B communicate directly. If a malicious actor, Device C, intercepts their communication via ARP spoofing, Wireshark can reveal duplicate ARP replies with differing MAC addresses for the same IP.
Signs of an ARP Spoofing Attack
| Indicator | Description | Wireshark Feature |
|---|---|---|
| Duplicate ARP responses | Same IP associated with multiple MACs | Packet List and ARP filters |
| Unexpected MAC addresses | Unknown MACs appear in ARP replies | Packet Details Pane |
| Increased ARP traffic | Large volume of ARP requests and replies | Capture Statistics |
Advanced Tip:
Configure a script in Wireshark’s Lua interpreter to trigger alerts when duplicate ARP replies are detected.
-- Lua script to detect duplicate ARP replies in Wireshark
-- Save this script as arp_alert.lua and load it in Wireshark's Lua interpreter
-- Register a protocol
local arp_alert = Proto("ARPAlert", "Duplicate ARP Alert")
-- Add a field to monitor ARP replies
local arp_ip_field = Field.new("arp.src.proto_ipv4")
local arp_mac_field = Field.new("arp.src.hw_mac")
-- Table to track duplicate ARP replies
local arp_cache = {}
-- Function to dissect packets
function arp_alert.dissector(buffer, pinfo, tree)
-- Check if the packet is an ARP packet
if pinfo.cols.protocol == "ARP" then
-- Extract ARP source IP and MAC address
local src_ip = tostring(arp_ip_field())
local src_mac = tostring(arp_mac_field())
if src_ip and src_mac then
-- Check if the IP address already exists in the cache
if arp_cache[src_ip] and arp_cache[src_ip] ~= src_mac then
-- Duplicate ARP detected
print("Duplicate ARP reply detected!")
print(string.format("IP: %s is now associated with MAC: %s (previous: %s)", src_ip, src_mac, arp_cache[src_ip]))
-- Add an expert info alert
local subtree = tree:add(arp_alert, buffer(), "Duplicate ARP Alert")
subtree:add_expert_info(PI_SECURITY, PI_WARN, string.format("Duplicate ARP reply detected for IP: %s", src_ip))
end
-- Update the ARP cache
arp_cache[src_ip] = src_mac
end
end
end
-- Register the dissector for ARP packets
local eth_type = DissectorTable.get("ethertype")
eth_type:add(0x0806, arp_alert)
2. Identifying Data Exfiltration
Data exfiltration involves unauthorized transfer of sensitive information outside the organization. This is often achieved through covert channels or by exploiting legitimate protocols.
How Wireshark Helps:
- Monitor outbound traffic for abnormal patterns, such as excessive data transfer to unknown IPs.
- Inspect HTTP, DNS, or custom protocol traffic for encoded payloads or suspicious domains.
Configuration Steps:
- Set Capture Filters:
- Use tcp port 443 and not host 192.168.1.0/24 to capture outbound HTTPS traffic.
- Analyze Streams:
- Right-click on a suspicious packet and select Follow > TCP Stream to reconstruct data flows.
- Focus on Packet Size:
- Apply a display filter like frame.len > 1500 to find unusually large packets.
Example:
An employee’s workstation is observed sending a large amount of data to an external IP. Wireshark highlights the transfer, and further analysis of the stream reveals sensitive files being sent through encrypted HTTPS.
Identifying Signs of Data Exfiltration
| Indicator | Description | Wireshark Feature |
|---|---|---|
| Large outbound packets | Packets larger than normal threshold sizes | Frame length filters |
| Frequent unknown IP connections | Connections to unfamiliar external IPs | Packet List and IP filters |
| Suspicious DNS queries | Lookups for uncommon or unrelated domains | DNS protocol analysis |
Advanced Tip:
Leverage the Wireshark “Expert Information” feature under Analyze > Expert Information to identify abnormal behaviors, such as retransmissions or protocol anomalies.
3. Decrypting TLS Traffic
TLS encryption protects data in transit, but for analysis purposes, it may be necessary to decrypt this traffic. Wireshark supports decryption of TLS traffic when provided with the appropriate session keys.
How Wireshark Helps:
- Examine encrypted traffic to identify anomalies or validate secure communication.
- Troubleshoot issues with certificate exchanges and handshakes.
Configuration Steps:
- Obtain Session Keys:
- Enable logging of session keys in your browser (e.g., Chrome: –ssl-key-log-file)
- Configure Wireshark:
- Go to Edit > Preferences > Protocols > TLS and specify the path to the key log file.
- Apply Filters:
- Use tls.handshake.type == 1 to isolate client hello packets.
Example:
Analyzing encrypted traffic reveals a handshake failure due to an expired certificate. Wireshark displays the root cause in the handshake sequence.
Advanced Tip:
For enterprise-grade setups, integrate Wireshark with a decryption proxy or use pre-master secrets from a load balancer to capture all relevant traffic.
4. Analyzing Malware Command-and-Control (C2) Communication
Malware often communicates with C2 servers for instructions. Detecting and analyzing this traffic is crucial for containment and remediation.
How Wireshark Helps:
- Identify unusual DNS queries or HTTP headers used by malware.
- Follow streams to understand the sequence of commands and responses.
Configuration Steps:
- Set DNS Filters:
- Use dns or http.request to isolate queries and requests.
- Inspect Queries:
- Look for suspicious domains or subdomains like .onion or random alphanumeric strings.
- Follow Streams:
- Analyze specific TCP or UDP streams for encoded payloads.
Detecting C2 Communication
| Indicator | Description | Wireshark Feature |
|---|---|---|
| Odd DNS queries | Requests to suspicious domains | DNS filters |
| Custom HTTP headers | Headers not typical for legitimate applications | HTTP protocol analysis |
| Repeated small payload sizes | Uniformly sized packets to one IP | TCP/UDP stream analysis |
Advanced Tip:
Create custom dissectors in Lua to parse proprietary malware protocols.
5. Troubleshooting Advanced Protocols (e.g., QUIC, SCTP)
Modern protocols like QUIC and SCTP offer advanced capabilities but can complicate troubleshooting without proper tools.
How Wireshark Helps:
- Decode headers and payloads to understand protocol behavior.
- Diagnose issues like connection failures or performance bottlenecks.
Configuration Steps:
- Enable Protocol Preferences:
- For QUIC: Go to Edit > Preferences > Protocols > QUIC and ensure the dissector is enabled.
- For SCTP: Enable reassembly under Edit > Preferences > Protocols > SCTP.
- Follow Streams:
- Use Follow > UDP Stream for QUIC or Follow > SCTP Stream for SCTP.
- Apply Filters:
- Example for QUIC: quic.stream_id == 0.
- Example for SCTP: sctp.assoc_id == 1.
Advanced Protocol Analysis
| Protocol | Troubleshooting Focus | Wireshark Features |
|---|---|---|
| QUIC | Connection issues, retransmissions | Stream analysis, QUIC filters |
| SCTP | Multi-homing, association management | SCTP dissectors, packet reassembly |
Advanced Tip:
Utilize Wireshark’s graphing tools under Statistics > I/O Graph to visualize QUIC retransmissions or SCTP multi-homing performance.
Best Practices for Using Wireshark in Cybersecurity
- Start with Specific Filters:
- Always use capture and display filters to narrow down data to the relevant packets.
- Leverage Custom Profiles:
- Create profiles tailored to specific tasks, such as malware analysis or TLS decryption.
- Automate with Lua Scripts:
- Use Lua to write custom dissectors or automate repetitive tasks.
- Integrate with Other Tools:
- Pair Wireshark with Zeek or Suricata for a comprehensive analysis.
- Document Findings:
- Use Wireshark’s annotation tools to add comments to packets and save PCAPs for future reference.
FAQ’s
How do I start capturing network traffic for analysis?
To start capturing network traffic, you should first set up a packet capture tool. This tool will allow you to gather network data, including network packets and data packets, for comprehensive network traffic analysis. Ensure that your setup aligns with the needs of your network administrators and network analysis objectives.
What steps are involved in network traffic analysis?
Network traffic analysis involves monitoring and inspecting network traffic to identify trends, issues, or unauthorized access attempts. Using a packet capture or packet sniffer tool, you can collect packet data, which helps in troubleshooting network issues and ensures the integrity of network communication.
What tools can assist with network troubleshooting and inspecting traffic?
For effective network troubleshooting, tools like packet sniffers and network analysis platforms are useful. They help inspect network traffic and identify network vulnerabilities, enabling administrators to address and resolve issues promptly. Such tools also assist in capturing network traffic for detailed review.
How do network administrators manage network vulnerabilities?
Network administrators manage network vulnerabilities by routinely inspecting network traffic and leveraging tools for capturing network traffic and displaying packets. By analyzing network data and conducting thorough network traffic analysis, they can detect and mitigate potential security threats proactively.
How can I analyze network traffic for security analysis?
To analyze network traffic effectively for security analysis, use tools that enable security professionals to capture network packets and inspect packets. Such tools often have a graphical user interface that helps visualize insights and communication patterns, which can reveal potential network problems or unauthorized activities.
What role do network engineers play in handling network activities?
Network engineers are pivotal in managing network activities. They utilize intrusion detection systems and various tools to capture network packets and sniff traffic. By identifying packet payloads and monitoring security alerts, engineers can promptly address network vulnerabilities and maintain the integrity of the operating systems.
How can security professionals utilize a graphical user interface for intrusion detection?
Security professionals often rely on a graphical user interface to monitor intrusion detection systems. This interface simplifies the process of capturing and displaying network traffic and packet payloads. It offers valuable tools for visualizing insights and addressing malware infections or other network problems efficiently.
Conclusion
Wireshark is an indispensable tool for cybersecurity professionals, offering deep insights into network traffic and enabling precise analysis of potential threats. Whether detecting MitM attacks, identifying data exfiltration, decrypting TLS traffic, or analyzing advanced protocols, Wireshark’s versatility and power make it a cornerstone of network security. By mastering its advanced features and configurations, you can turn Wireshark into your ultimate ally in defending against cyber threats.

Wireshark is a powerful network protocol analyzer widely regarded as an essential tool in cybersecurity. From incident response to forensic investigations, it empowers cybersecurity professionals to monitor, analyze, and troubleshoot network traffic. In this comprehensive guide, we will delve into how Wireshark is used in cybersecurity, with intermediate to advanced examples, step-by-step configurations, and actionable insights to help you master this indispensable tool.
What is Wireshark?
Wireshark captures packets—the basic units of data transmission—traveling across a network. These packets are dissected and presented in a human-readable format for analysis. Wireshark supports thousands of protocols and can be customized for specific use cases, making it an essential component of a cybersecurity professional’s toolkit.
Wireshark operates by placing a network interface into promiscuous mode, capturing all traffic traversing the network. With its advanced filtering, coloring, and dissecting capabilities, Wireshark is ideal for uncovering network anomalies, debugging issues, and investigating potential threats.
Use Cases for Wireshark in Cybersecurity
1. Detecting Man-in-the-Middle (MitM) Attacks
MitM attacks occur when a malicious actor intercepts communications between two parties. These attacks often rely on ARP (Address Resolution Protocol) spoofing to redirect traffic.
How Wireshark Helps:
- Detect anomalous ARP packets, such as duplicate IP addresses assigned to different MAC addresses.
- Identify changes in normal traffic flow, such as unexpected routing through unknown devices.
Configuration Steps:
- Set Filters for ARP Traffic:
- Use the capture filter arp to isolate ARP packets.
- Examine Duplicate Responses:
- Look for repeated Who has and is at messages in the Packet List Pane.
- Visualize Suspicious Patterns:
- Customize the coloring rules under View > Coloring Rules to highlight ARP packets from unexpected sources.

Example:
Consider a scenario where Device A and Device B communicate directly. If a malicious actor, Device C, intercepts their communication via ARP spoofing, Wireshark can reveal duplicate ARP replies with differing MAC addresses for the same IP.
Signs of an ARP Spoofing Attack
| Indicator | Description | Wireshark Feature |
|---|---|---|
| Duplicate ARP responses | Same IP associated with multiple MACs | Packet List and ARP filters |
| Unexpected MAC addresses | Unknown MACs appear in ARP replies | Packet Details Pane |
| Increased ARP traffic | Large volume of ARP requests and replies | Capture Statistics |
Advanced Tip:
Configure a script in Wireshark’s Lua interpreter to trigger alerts when duplicate ARP replies are detected.
-- Lua script to detect duplicate ARP replies in Wireshark
-- Save this script as arp_alert.lua and load it in Wireshark's Lua interpreter
-- Register a protocol
local arp_alert = Proto("ARPAlert", "Duplicate ARP Alert")
-- Add a field to monitor ARP replies
local arp_ip_field = Field.new("arp.src.proto_ipv4")
local arp_mac_field = Field.new("arp.src.hw_mac")
-- Table to track duplicate ARP replies
local arp_cache = {}
-- Function to dissect packets
function arp_alert.dissector(buffer, pinfo, tree)
-- Check if the packet is an ARP packet
if pinfo.cols.protocol == "ARP" then
-- Extract ARP source IP and MAC address
local src_ip = tostring(arp_ip_field())
local src_mac = tostring(arp_mac_field())
if src_ip and src_mac then
-- Check if the IP address already exists in the cache
if arp_cache[src_ip] and arp_cache[src_ip] ~= src_mac then
-- Duplicate ARP detected
print("Duplicate ARP reply detected!")
print(string.format("IP: %s is now associated with MAC: %s (previous: %s)", src_ip, src_mac, arp_cache[src_ip]))
-- Add an expert info alert
local subtree = tree:add(arp_alert, buffer(), "Duplicate ARP Alert")
subtree:add_expert_info(PI_SECURITY, PI_WARN, string.format("Duplicate ARP reply detected for IP: %s", src_ip))
end
-- Update the ARP cache
arp_cache[src_ip] = src_mac
end
end
end
-- Register the dissector for ARP packets
local eth_type = DissectorTable.get("ethertype")
eth_type:add(0x0806, arp_alert)
2. Identifying Data Exfiltration
Data exfiltration involves unauthorized transfer of sensitive information outside the organization. This is often achieved through covert channels or by exploiting legitimate protocols.
How Wireshark Helps:
- Monitor outbound traffic for abnormal patterns, such as excessive data transfer to unknown IPs.
- Inspect HTTP, DNS, or custom protocol traffic for encoded payloads or suspicious domains.
Configuration Steps:
- Set Capture Filters:
- Use tcp port 443 and not host 192.168.1.0/24 to capture outbound HTTPS traffic.
- Analyze Streams:
- Right-click on a suspicious packet and select Follow > TCP Stream to reconstruct data flows.
- Focus on Packet Size:
- Apply a display filter like frame.len > 1500 to find unusually large packets.
Example:
An employee’s workstation is observed sending a large amount of data to an external IP. Wireshark highlights the transfer, and further analysis of the stream reveals sensitive files being sent through encrypted HTTPS.
Identifying Signs of Data Exfiltration
| Indicator | Description | Wireshark Feature |
|---|---|---|
| Large outbound packets | Packets larger than normal threshold sizes | Frame length filters |
| Frequent unknown IP connections | Connections to unfamiliar external IPs | Packet List and IP filters |
| Suspicious DNS queries | Lookups for uncommon or unrelated domains | DNS protocol analysis |
Advanced Tip:
Leverage the Wireshark “Expert Information” feature under Analyze > Expert Information to identify abnormal behaviors, such as retransmissions or protocol anomalies.
3. Decrypting TLS Traffic
TLS encryption protects data in transit, but for analysis purposes, it may be necessary to decrypt this traffic. Wireshark supports decryption of TLS traffic when provided with the appropriate session keys.
How Wireshark Helps:
- Examine encrypted traffic to identify anomalies or validate secure communication.
- Troubleshoot issues with certificate exchanges and handshakes.
Configuration Steps:
- Obtain Session Keys:
- Enable logging of session keys in your browser (e.g., Chrome: –ssl-key-log-file)
- Configure Wireshark:
- Go to Edit > Preferences > Protocols > TLS and specify the path to the key log file.
- Apply Filters:
- Use tls.handshake.type == 1 to isolate client hello packets.
Example:
Analyzing encrypted traffic reveals a handshake failure due to an expired certificate. Wireshark displays the root cause in the handshake sequence.
Advanced Tip:
For enterprise-grade setups, integrate Wireshark with a decryption proxy or use pre-master secrets from a load balancer to capture all relevant traffic.
4. Analyzing Malware Command-and-Control (C2) Communication
Malware often communicates with C2 servers for instructions. Detecting and analyzing this traffic is crucial for containment and remediation.
How Wireshark Helps:
- Identify unusual DNS queries or HTTP headers used by malware.
- Follow streams to understand the sequence of commands and responses.
Configuration Steps:
- Set DNS Filters:
- Use dns or http.request to isolate queries and requests.
- Inspect Queries:
- Look for suspicious domains or subdomains like .onion or random alphanumeric strings.
- Follow Streams:
- Analyze specific TCP or UDP streams for encoded payloads.
Detecting C2 Communication
| Indicator | Description | Wireshark Feature |
|---|---|---|
| Odd DNS queries | Requests to suspicious domains | DNS filters |
| Custom HTTP headers | Headers not typical for legitimate applications | HTTP protocol analysis |
| Repeated small payload sizes | Uniformly sized packets to one IP | TCP/UDP stream analysis |
Advanced Tip:
Create custom dissectors in Lua to parse proprietary malware protocols.
5. Troubleshooting Advanced Protocols (e.g., QUIC, SCTP)
Modern protocols like QUIC and SCTP offer advanced capabilities but can complicate troubleshooting without proper tools.
How Wireshark Helps:
- Decode headers and payloads to understand protocol behavior.
- Diagnose issues like connection failures or performance bottlenecks.
Configuration Steps:
- Enable Protocol Preferences:
- For QUIC: Go to Edit > Preferences > Protocols > QUIC and ensure the dissector is enabled.
- For SCTP: Enable reassembly under Edit > Preferences > Protocols > SCTP.
- Follow Streams:
- Use Follow > UDP Stream for QUIC or Follow > SCTP Stream for SCTP.
- Apply Filters:
- Example for QUIC: quic.stream_id == 0.
- Example for SCTP: sctp.assoc_id == 1.
Advanced Protocol Analysis
| Protocol | Troubleshooting Focus | Wireshark Features |
|---|---|---|
| QUIC | Connection issues, retransmissions | Stream analysis, QUIC filters |
| SCTP | Multi-homing, association management | SCTP dissectors, packet reassembly |
Advanced Tip:
Utilize Wireshark’s graphing tools under Statistics > I/O Graph to visualize QUIC retransmissions or SCTP multi-homing performance.
Best Practices for Using Wireshark in Cybersecurity
- Start with Specific Filters:
- Always use capture and display filters to narrow down data to the relevant packets.
- Leverage Custom Profiles:
- Create profiles tailored to specific tasks, such as malware analysis or TLS decryption.
- Automate with Lua Scripts:
- Use Lua to write custom dissectors or automate repetitive tasks.
- Integrate with Other Tools:
- Pair Wireshark with Zeek or Suricata for a comprehensive analysis.
- Document Findings:
- Use Wireshark’s annotation tools to add comments to packets and save PCAPs for future reference.
FAQ’s
How do I start capturing network traffic for analysis?
To start capturing network traffic, you should first set up a packet capture tool. This tool will allow you to gather network data, including network packets and data packets, for comprehensive network traffic analysis. Ensure that your setup aligns with the needs of your network administrators and network analysis objectives.
What steps are involved in network traffic analysis?
Network traffic analysis involves monitoring and inspecting network traffic to identify trends, issues, or unauthorized access attempts. Using a packet capture or packet sniffer tool, you can collect packet data, which helps in troubleshooting network issues and ensures the integrity of network communication.
What tools can assist with network troubleshooting and inspecting traffic?
For effective network troubleshooting, tools like packet sniffers and network analysis platforms are useful. They help inspect network traffic and identify network vulnerabilities, enabling administrators to address and resolve issues promptly. Such tools also assist in capturing network traffic for detailed review.
How do network administrators manage network vulnerabilities?
Network administrators manage network vulnerabilities by routinely inspecting network traffic and leveraging tools for capturing network traffic and displaying packets. By analyzing network data and conducting thorough network traffic analysis, they can detect and mitigate potential security threats proactively.
How can I analyze network traffic for security analysis?
To analyze network traffic effectively for security analysis, use tools that enable security professionals to capture network packets and inspect packets. Such tools often have a graphical user interface that helps visualize insights and communication patterns, which can reveal potential network problems or unauthorized activities.
What role do network engineers play in handling network activities?
Network engineers are pivotal in managing network activities. They utilize intrusion detection systems and various tools to capture network packets and sniff traffic. By identifying packet payloads and monitoring security alerts, engineers can promptly address network vulnerabilities and maintain the integrity of the operating systems.
How can security professionals utilize a graphical user interface for intrusion detection?
Security professionals often rely on a graphical user interface to monitor intrusion detection systems. This interface simplifies the process of capturing and displaying network traffic and packet payloads. It offers valuable tools for visualizing insights and addressing malware infections or other network problems efficiently.
Conclusion
Wireshark is an indispensable tool for cybersecurity professionals, offering deep insights into network traffic and enabling precise analysis of potential threats. Whether detecting MitM attacks, identifying data exfiltration, decrypting TLS traffic, or analyzing advanced protocols, Wireshark’s versatility and power make it a cornerstone of network security. By mastering its advanced features and configurations, you can turn Wireshark into your ultimate ally in defending against cyber threats.