As a cybersecurity engineer with extensive experience in Security Information and Event Management (SIEM) systems, I understand the critical importance of scalability and reliability in security solutions. One question that often arises is: “How many endpoints can Wazuh handle?” This inquiry is vital for organizations planning to implement or expand their security infrastructure. In this comprehensive analysis, we will explore Wazuh’s scalability, supported by real-world case studies, to provide a clear understanding of its capabilities.
How Many Endpoints Can Wazuh Handle? Understanding Wazuh’s Architecture
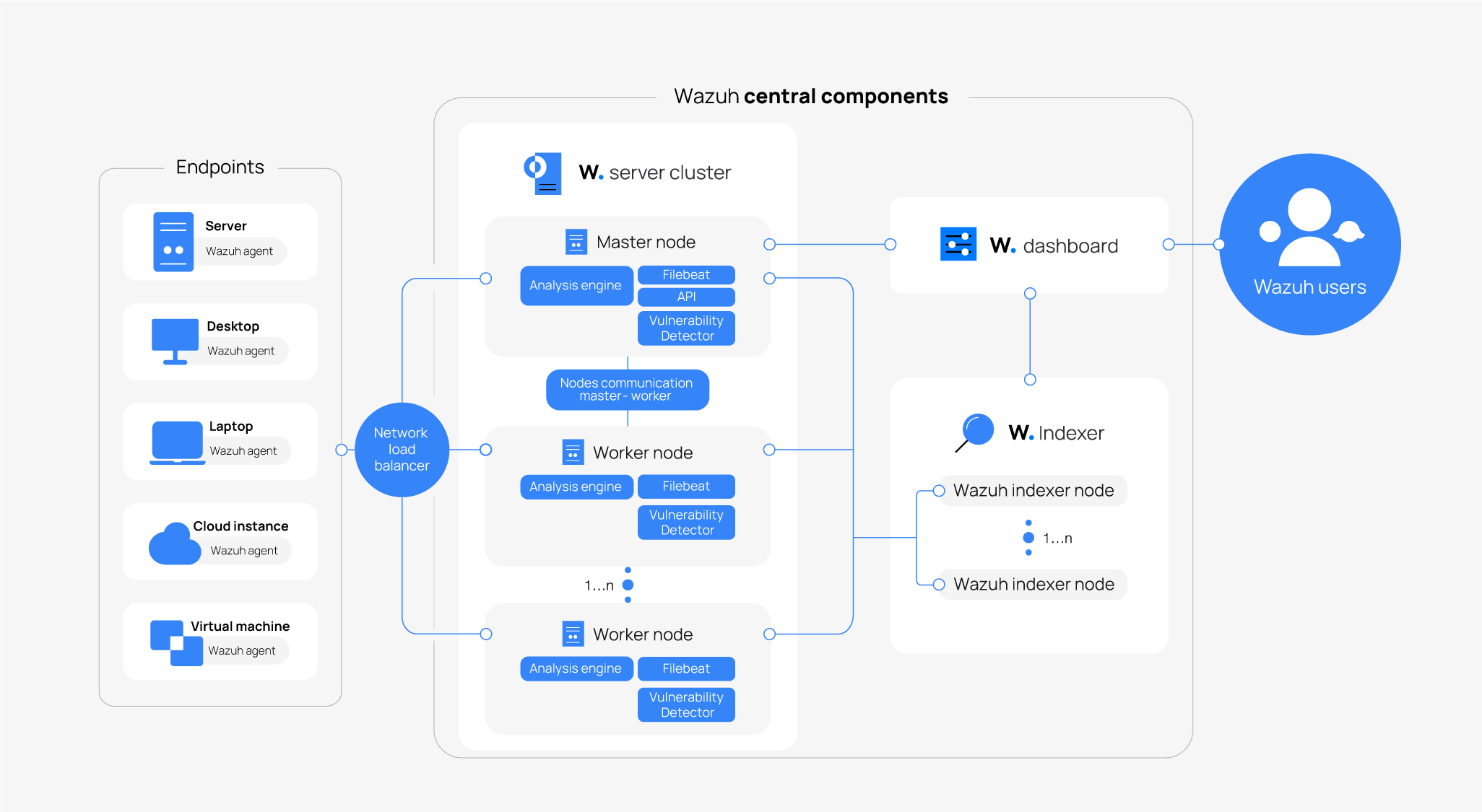
Wazuh is an open-source security solution that combines Extended Detection and Response (XDR) with SIEM functionalities in a unified platform. Its architecture is designed for scalability and flexibility, comprising the following key components:
- Agents: Lightweight modules installed on endpoints (e.g., servers, workstations) to collect security data.
- Manager: Central server that processes data received from agents, analyzes it, and generates alert data when specific security events trigger rules.
- Indexer: Stores and indexes the data for efficient search and retrieval.
- Dashboard: Provides a user-friendly interface for visualization and management.
This modular design allows Wazuh to adapt to various organizational needs, from small businesses to large enterprises.
Overview of Wazuh Components
Wazuh is a comprehensive security monitoring and compliance tool that consists of several key components. These components work together to provide real-time threat detection, incident response, and security monitoring capabilities. The main components of Wazuh include:
- Wazuh Server: The central component of the Wazuh architecture, responsible for collecting and analyzing data from monitored endpoints and network devices. It processes the data to identify potential security threats and generates alerts accordingly.
- Wazuh Manager: The management interface for the Wazuh Server, used to configure and manage the Wazuh deployment. It allows administrators to set up rules, manage agents, and oversee the overall security posture.
- Wazuh Agent: A lightweight agent installed on monitored endpoints, responsible for collecting and forwarding log data to the Wazuh Server. These agents are crucial for gathering detailed security information from various systems.
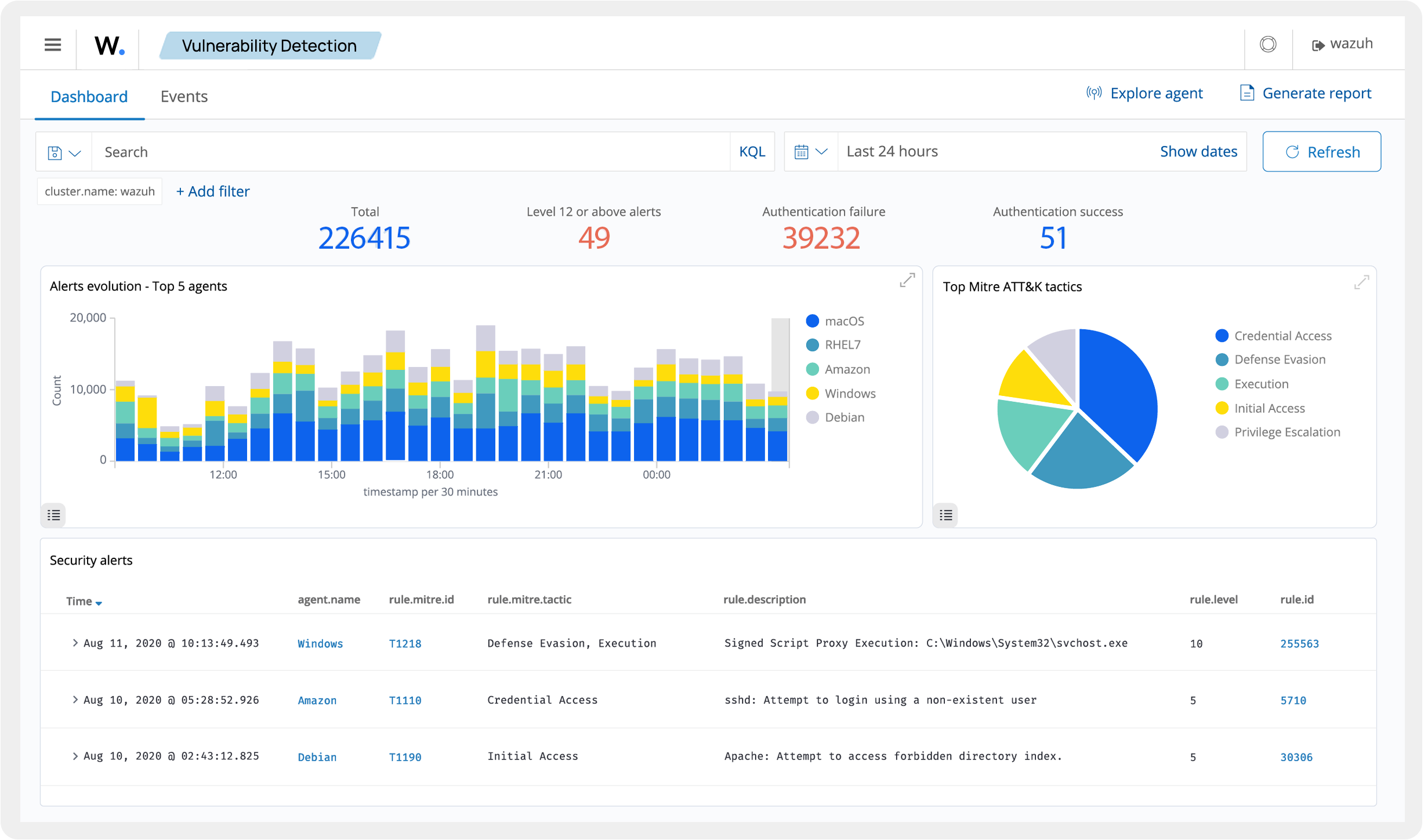
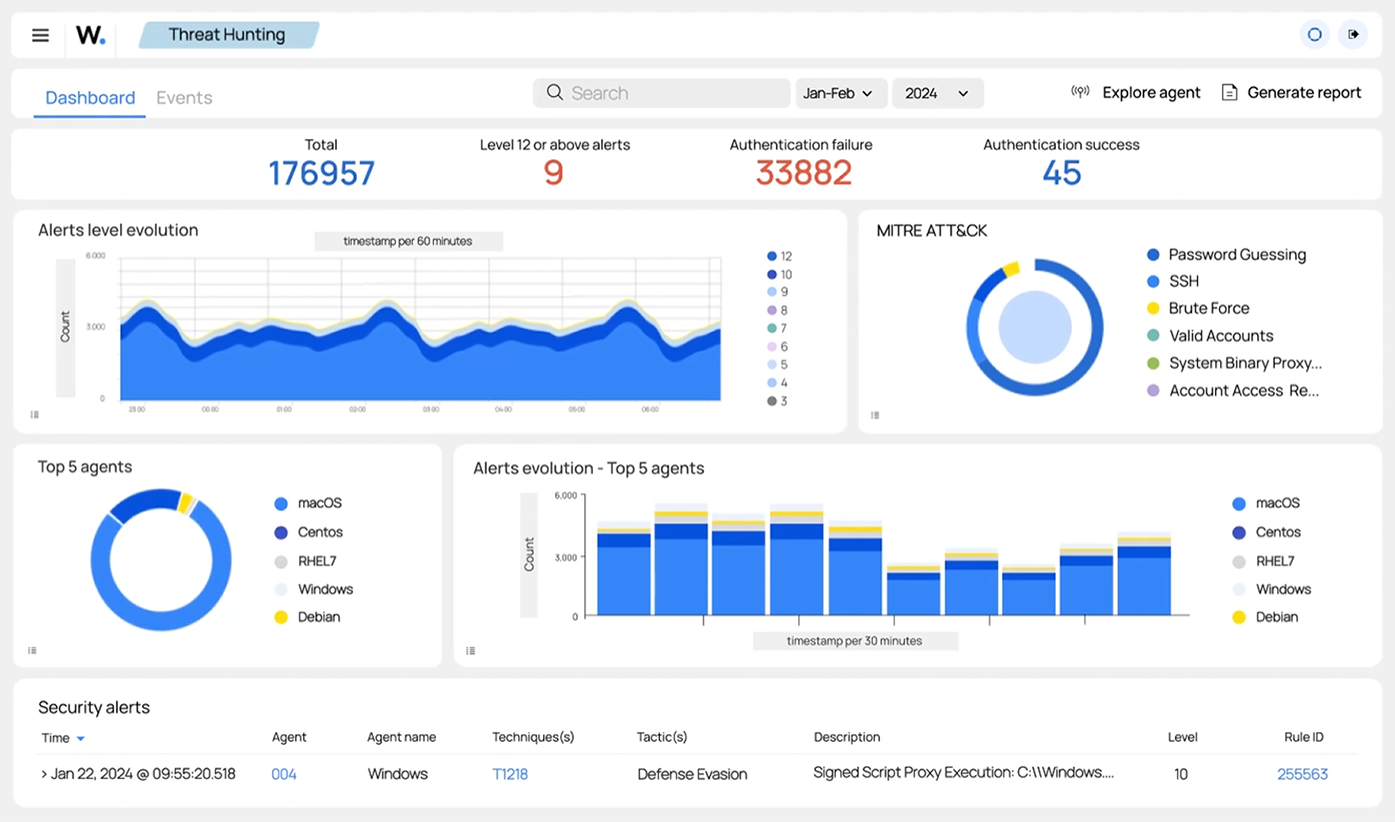
- Wazuh Dashboard: A web-based interface for visualizing and analyzing security data, providing real-time insights into security threats and incidents. The dashboard offers a user-friendly way to monitor the security status and respond to alerts.
These components form a robust framework that ensures comprehensive security monitoring and management across an organization’s IT infrastructure.
Core Architecture
| Component | Role | Scalability Impact |
|---|---|---|
| Agent | Collects logs and events | Lightweight; scales with endpoints |
| Manager | Analyzes data, generates alerts. The configuration process involves setting up YARA to scan for malware on various endpoints. | Can cluster to handle larger environments |
| Elasticsearch | Stores indexed log data | Critical for high data throughput |
| Dashboard | Visualization and analytics | Scales based on user interaction and queries |
Communication and Data Flow
The Wazuh components communicate with each other through a secure and encrypted protocol, ensuring the integrity and confidentiality of the data. The data flow between Wazuh components is structured to optimize efficiency and security:
- Wazuh Agent: Collects log data from monitored endpoints and forwards it to the Wazuh Server. The agent ensures that all relevant security events are captured and transmitted securely.
- Wazuh Server: Analyzes the log data received from the agents and generates alerts based on predefined rules. The server’s analysis capabilities are critical for identifying potential security threats in real-time.
- Wazuh Manager: Configures and manages the Wazuh deployment, including the Wazuh Server and Wazuh Agents. It provides a centralized interface for administrators to manage the entire security monitoring setup.
- Wazuh Dashboard: Visualizes and analyzes security data, providing real-time insights into security threats and incidents. The dashboard allows users to interact with the data, generate reports, and take necessary actions based on the alerts.
This structured data flow ensures that security information is collected, analyzed, and presented efficiently, enabling rapid detection and response to security incidents.
Data Storage and Management
Wazuh stores log data and alert information in a centralized database, allowing for efficient querying and analysis of security data. The Wazuh Server is responsible for storing and managing the log data, ensuring that it is readily available for analysis and reporting.
The Wazuh Manager provides an interface for configuring and managing data storage and retention policies. This includes setting up data compression, encryption, and rotation to ensure that log data is stored securely and efficiently. These features help in maintaining the integrity and availability of security data while optimizing storage resources.
By implementing robust data storage and management practices, Wazuh ensures that security data is both secure and accessible, facilitating effective security monitoring and compliance reporting.
Scalability of Wazuh
The scalability of Wazuh depends on several factors, including hardware resources, network infrastructure, and configuration settings. While specific numerical limits are not explicitly documented, Wazuh’s architecture supports significant scalability through:
- Standalone Manager: Capable of supporting up to 10,000 endpoints with robust hardware.
- Elastic Stack Integration: Utilizing Elasticsearch as the indexer enables efficient data storage and retrieval, supporting scalability in data handling.
- Clustered Deployment: Implementing a cluster of Wazuh managers can distribute the load effectively, allowing the system to handle a large number of agents. Scales to 100,000+ endpoints when distributed across multiple managers and Elasticsearch nodes.
It’s important to note that exceeding the maximum number of active agents without proper scaling measures may lead to system instability. Therefore, planning and implementing appropriate scaling strategies are crucial for maintaining system performance.
Wazuh Server Requirements
The following table outlines typical hardware requirements for scaling Wazuh.
| Endpoints | CPU (Cores) | RAM (GB) | Storage (SSD) | Clustered? |
|---|---|---|---|---|
| 1,000 | 8 | 16 | 500GB | No |
| 10,000 | 16 | 64 | 1TB | Optional |
| 50,000+ | 32+ | 128+ | 2TB+ | Yes, especially in production environments |
Log Collection and Forwarding
Wazuh provides a flexible and scalable log collection and forwarding mechanism, allowing for the collection of log data from a wide range of sources. This includes:
- Monitored Endpoints: Wazuh Agents collect log data from monitored endpoints and forward it to the Wazuh Server. This ensures that detailed security information from various systems is captured and analyzed.
- Network Devices: Wazuh supports the collection of log data from network devices, such as firewalls and routers. This capability extends Wazuh’s monitoring reach to critical network infrastructure.
- Operating System Logs: Wazuh can collect log data from operating system logs, such as Windows Event Logs and Linux syslog. This allows for comprehensive monitoring of system-level events.
Wazuh also provides features for log filtering, normalization, and enrichment, ensuring that log data is collected and forwarded in a standardized and actionable format. These capabilities enhance the quality and relevance of the data used for security analysis.
Security Monitoring
Wazuh provides real-time security monitoring capabilities, allowing for the detection and response to security threats and incidents. Wazuh’s security monitoring features include:
- Threat Detection: Wazuh’s threat detection engine analyzes log data and identifies potential security threats. This proactive approach helps in identifying and mitigating risks before they can cause significant damage.
- Incident Response: Wazuh provides features for incident response, including alerting, reporting, and remediation. These tools enable organizations to respond quickly and effectively to security incidents.
- Compliance Monitoring: Wazuh provides features for compliance monitoring, including reporting and auditing. This helps organizations ensure that they meet regulatory requirements and maintain a strong security posture.
Wazuh’s security monitoring features are designed to provide real-time insights into security threats and incidents, allowing for rapid detection and response. This comprehensive approach ensures that organizations can maintain a robust and proactive security strategy.
Real-World Case Studies
To illustrate Wazuh’s scalability and effectiveness, let’s examine some real-world implementations:
1. Groupon’s Deployment of Wazuh to Protect and Monitor AWS
Groupon, a global e-commerce marketplace, integrated Wazuh into its security infrastructure to monitor and protect its Amazon Web Services (AWS) environment. By deploying Wazuh, Groupon enhanced its security visibility and improved metrics while reducing costs. This case demonstrates Wazuh’s capability to scale within cloud environments and integrate seamlessly with existing systems.
2. University of Chichester’s Proactive Defense with Wazuh
The University of Chichester implemented Wazuh to strengthen its cybersecurity posture. By leveraging Wazuh’s comprehensive monitoring and alerting features, the university achieved a proactive defense strategy, ensuring the protection of its critical assets. This example highlights Wazuh’s adaptability to various organizational structures and its effectiveness in educational institutions.
3. Guayoyo’s Virtual SOC Triumph with Wazuh
Guayoyo, a cybersecurity service provider, utilized Wazuh to establish a virtual Security Operations Center (SOC). By integrating Wazuh into their operations, they provided enhanced security monitoring and incident response services to their clients. This case underscores Wazuh’s flexibility and its suitability for managed security service providers.
Performance and Scalability Metrics
Endpoint Management Across Deployment Types with Wazuh Agents
The following chart illustrates Wazuh’s endpoint scalability in various deployment configurations.
import matplotlib.pyplot as plt
# Data for chart
endpoints = [1000, 10000, 50000, 100000]
cpu_cores = [8, 16, 32, 64]
plt.figure(figsize=(8, 6))
plt.plot(endpoints, cpu_cores, marker='o', label='CPU Cores')
plt.title('Hardware Requirements for Endpoint Scalability')
plt.xlabel('Number of Endpoints')
plt.ylabel('CPU Cores')
plt.grid(True)
plt.legend()
plt.show()
Key Considerations for Scaling Wazuh: Configuration Process
When planning to scale Wazuh to accommodate a large number of endpoints, consider the following factors:
- Hardware Resources: Ensure that the servers hosting Wazuh components have adequate CPU, memory, and storage to handle the anticipated load.
- Network Infrastructure: A robust and low-latency network is essential for efficient communication between agents and the manager.
- Configuration Optimization: Fine-tune Wazuh’s configuration settings, such as event throughput limits, to align with your organization’s specific needs.
- Regular Monitoring and Maintenance: Continuously monitor system performance and conduct regular maintenance to prevent potential issues related to scalability. Regular checks will help ensure that the environment is working properly and meets the necessary requirements.
FAQ’s
How can I verify my wazuh documentation with a Python script?
To verify the wazuh documentation, you can use a Python script. First, ensure your installation is correct by using a test script. The Python script can execute various tests, check for errors, and verify connections, ensuring all commands are functioning as expected. This process often involves checking monitored files and ensuring messages are transmitted correctly.
What is the best way to create a command for file monitoring?
Creating a command to monitor files involves using the following command structure in your script or directory. It’s crucial to specify parameters for the monitored files and to test the command with the same test across different paths. This way, you can verify if it’s effective in detecting changes or blocked access attempts.
How do I modify the username for a version update?
To modify the username for a version update in your script, specify the correct parameters in your script and execute the required commands. You can use a Python script to automate this process, ensuring that the settings are updated in your directory according to the new version guidelines.
What should I do if I detect an error during installation?
If an error is detected during installation, first check the wazuh documentation for the exact rule ID and error descriptions. Verify the connection and parameters used during installation. Follow the correct commands to resolve the error, and consider modifying your script if necessary. This helps ensure your installation and system operate smoothly.
What is the role of the Wazuh manager in system monitoring?
The Wazuh manager is a central component in system monitoring, responsible for handling data collection, analysis, and storage. It processes alerts from monitored files and identifies any inconsistencies or security events. By integrating with the wazuh dashboard, the Wazuh manager offers real-time insights and comprehensive control over system activities.
How can the Wazuh dashboard improve security management?
The Wazuh dashboard provides a user-friendly interface for viewing security events managed by the Wazuh manager. It allows users to visualize data, assess vulnerabilities, and track the status of alerts in real time. This integration ensures efficient oversight of potential threats and facilitates quick responses to detected issues.
Conclusion
Determining the exact number of endpoints Wazuh can handle depends on various factors, including system architecture, resource allocation, and specific use cases. While precise numerical limits are not explicitly stated in the available documentation, real-world implementations demonstrate Wazuh’s capability to scale effectively in diverse environments. By carefully planning and optimizing your deployment, Wazuh can serve as a robust and scalable security solution for your organization.

As a cybersecurity engineer with extensive experience in Security Information and Event Management (SIEM) systems, I understand the critical importance of scalability and reliability in security solutions. One question that often arises is: “How many endpoints can Wazuh handle?” This inquiry is vital for organizations planning to implement or expand their security infrastructure. In this comprehensive analysis, we will explore Wazuh’s scalability, supported by real-world case studies, to provide a clear understanding of its capabilities.
How Many Endpoints Can Wazuh Handle? Understanding Wazuh’s Architecture
Wazuh is an open-source security solution that combines Extended Detection and Response (XDR) with SIEM functionalities in a unified platform. Its architecture is designed for scalability and flexibility, comprising the following key components:
- Agents: Lightweight modules installed on endpoints (e.g., servers, workstations) to collect security data.
- Manager: Central server that processes data received from agents, analyzes it, and generates alert data when specific security events trigger rules.
- Indexer: Stores and indexes the data for efficient search and retrieval.
- Dashboard: Provides a user-friendly interface for visualization and management.
This modular design allows Wazuh to adapt to various organizational needs, from small businesses to large enterprises.
Overview of Wazuh Components
Wazuh is a comprehensive security monitoring and compliance tool that consists of several key components. These components work together to provide real-time threat detection, incident response, and security monitoring capabilities. The main components of Wazuh include:
- Wazuh Server: The central component of the Wazuh architecture, responsible for collecting and analyzing data from monitored endpoints and network devices. It processes the data to identify potential security threats and generates alerts accordingly.
- Wazuh Manager: The management interface for the Wazuh Server, used to configure and manage the Wazuh deployment. It allows administrators to set up rules, manage agents, and oversee the overall security posture.
- Wazuh Agent: A lightweight agent installed on monitored endpoints, responsible for collecting and forwarding log data to the Wazuh Server. These agents are crucial for gathering detailed security information from various systems.
- Wazuh Dashboard: A web-based interface for visualizing and analyzing security data, providing real-time insights into security threats and incidents. The dashboard offers a user-friendly way to monitor the security status and respond to alerts.
These components form a robust framework that ensures comprehensive security monitoring and management across an organization’s IT infrastructure.
Core Architecture
| Component | Role | Scalability Impact |
|---|---|---|
| Agent | Collects logs and events | Lightweight; scales with endpoints |
| Manager | Analyzes data, generates alerts. The configuration process involves setting up YARA to scan for malware on various endpoints. | Can cluster to handle larger environments |
| Elasticsearch | Stores indexed log data | Critical for high data throughput |
| Dashboard | Visualization and analytics | Scales based on user interaction and queries |
Communication and Data Flow
The Wazuh components communicate with each other through a secure and encrypted protocol, ensuring the integrity and confidentiality of the data. The data flow between Wazuh components is structured to optimize efficiency and security:
- Wazuh Agent: Collects log data from monitored endpoints and forwards it to the Wazuh Server. The agent ensures that all relevant security events are captured and transmitted securely.
- Wazuh Server: Analyzes the log data received from the agents and generates alerts based on predefined rules. The server’s analysis capabilities are critical for identifying potential security threats in real-time.
- Wazuh Manager: Configures and manages the Wazuh deployment, including the Wazuh Server and Wazuh Agents. It provides a centralized interface for administrators to manage the entire security monitoring setup.
- Wazuh Dashboard: Visualizes and analyzes security data, providing real-time insights into security threats and incidents. The dashboard allows users to interact with the data, generate reports, and take necessary actions based on the alerts.
This structured data flow ensures that security information is collected, analyzed, and presented efficiently, enabling rapid detection and response to security incidents.
Data Storage and Management
Wazuh stores log data and alert information in a centralized database, allowing for efficient querying and analysis of security data. The Wazuh Server is responsible for storing and managing the log data, ensuring that it is readily available for analysis and reporting.
The Wazuh Manager provides an interface for configuring and managing data storage and retention policies. This includes setting up data compression, encryption, and rotation to ensure that log data is stored securely and efficiently. These features help in maintaining the integrity and availability of security data while optimizing storage resources.
By implementing robust data storage and management practices, Wazuh ensures that security data is both secure and accessible, facilitating effective security monitoring and compliance reporting.
Scalability of Wazuh
The scalability of Wazuh depends on several factors, including hardware resources, network infrastructure, and configuration settings. While specific numerical limits are not explicitly documented, Wazuh’s architecture supports significant scalability through:
- Standalone Manager: Capable of supporting up to 10,000 endpoints with robust hardware.
- Elastic Stack Integration: Utilizing Elasticsearch as the indexer enables efficient data storage and retrieval, supporting scalability in data handling.
- Clustered Deployment: Implementing a cluster of Wazuh managers can distribute the load effectively, allowing the system to handle a large number of agents. Scales to 100,000+ endpoints when distributed across multiple managers and Elasticsearch nodes.
It’s important to note that exceeding the maximum number of active agents without proper scaling measures may lead to system instability. Therefore, planning and implementing appropriate scaling strategies are crucial for maintaining system performance.
Wazuh Server Requirements
The following table outlines typical hardware requirements for scaling Wazuh.
| Endpoints | CPU (Cores) | RAM (GB) | Storage (SSD) | Clustered? |
|---|---|---|---|---|
| 1,000 | 8 | 16 | 500GB | No |
| 10,000 | 16 | 64 | 1TB | Optional |
| 50,000+ | 32+ | 128+ | 2TB+ | Yes, especially in production environments |
Log Collection and Forwarding
Wazuh provides a flexible and scalable log collection and forwarding mechanism, allowing for the collection of log data from a wide range of sources. This includes:
- Monitored Endpoints: Wazuh Agents collect log data from monitored endpoints and forward it to the Wazuh Server. This ensures that detailed security information from various systems is captured and analyzed.
- Network Devices: Wazuh supports the collection of log data from network devices, such as firewalls and routers. This capability extends Wazuh’s monitoring reach to critical network infrastructure.
- Operating System Logs: Wazuh can collect log data from operating system logs, such as Windows Event Logs and Linux syslog. This allows for comprehensive monitoring of system-level events.
Wazuh also provides features for log filtering, normalization, and enrichment, ensuring that log data is collected and forwarded in a standardized and actionable format. These capabilities enhance the quality and relevance of the data used for security analysis.
Security Monitoring
Wazuh provides real-time security monitoring capabilities, allowing for the detection and response to security threats and incidents. Wazuh’s security monitoring features include:
- Threat Detection: Wazuh’s threat detection engine analyzes log data and identifies potential security threats. This proactive approach helps in identifying and mitigating risks before they can cause significant damage.
- Incident Response: Wazuh provides features for incident response, including alerting, reporting, and remediation. These tools enable organizations to respond quickly and effectively to security incidents.
- Compliance Monitoring: Wazuh provides features for compliance monitoring, including reporting and auditing. This helps organizations ensure that they meet regulatory requirements and maintain a strong security posture.
Wazuh’s security monitoring features are designed to provide real-time insights into security threats and incidents, allowing for rapid detection and response. This comprehensive approach ensures that organizations can maintain a robust and proactive security strategy.
Real-World Case Studies
To illustrate Wazuh’s scalability and effectiveness, let’s examine some real-world implementations:
1. Groupon’s Deployment of Wazuh to Protect and Monitor AWS
Groupon, a global e-commerce marketplace, integrated Wazuh into its security infrastructure to monitor and protect its Amazon Web Services (AWS) environment. By deploying Wazuh, Groupon enhanced its security visibility and improved metrics while reducing costs. This case demonstrates Wazuh’s capability to scale within cloud environments and integrate seamlessly with existing systems.
2. University of Chichester’s Proactive Defense with Wazuh
The University of Chichester implemented Wazuh to strengthen its cybersecurity posture. By leveraging Wazuh’s comprehensive monitoring and alerting features, the university achieved a proactive defense strategy, ensuring the protection of its critical assets. This example highlights Wazuh’s adaptability to various organizational structures and its effectiveness in educational institutions.
3. Guayoyo’s Virtual SOC Triumph with Wazuh
Guayoyo, a cybersecurity service provider, utilized Wazuh to establish a virtual Security Operations Center (SOC). By integrating Wazuh into their operations, they provided enhanced security monitoring and incident response services to their clients. This case underscores Wazuh’s flexibility and its suitability for managed security service providers.
Performance and Scalability Metrics
Endpoint Management Across Deployment Types with Wazuh Agents
The following chart illustrates Wazuh’s endpoint scalability in various deployment configurations.
import matplotlib.pyplot as plt
# Data for chart
endpoints = [1000, 10000, 50000, 100000]
cpu_cores = [8, 16, 32, 64]
plt.figure(figsize=(8, 6))
plt.plot(endpoints, cpu_cores, marker='o', label='CPU Cores')
plt.title('Hardware Requirements for Endpoint Scalability')
plt.xlabel('Number of Endpoints')
plt.ylabel('CPU Cores')
plt.grid(True)
plt.legend()
plt.show()
Key Considerations for Scaling Wazuh: Configuration Process
When planning to scale Wazuh to accommodate a large number of endpoints, consider the following factors:
- Hardware Resources: Ensure that the servers hosting Wazuh components have adequate CPU, memory, and storage to handle the anticipated load.
- Network Infrastructure: A robust and low-latency network is essential for efficient communication between agents and the manager.
- Configuration Optimization: Fine-tune Wazuh’s configuration settings, such as event throughput limits, to align with your organization’s specific needs.
- Regular Monitoring and Maintenance: Continuously monitor system performance and conduct regular maintenance to prevent potential issues related to scalability. Regular checks will help ensure that the environment is working properly and meets the necessary requirements.
FAQ’s
How can I verify my wazuh documentation with a Python script?
To verify the wazuh documentation, you can use a Python script. First, ensure your installation is correct by using a test script. The Python script can execute various tests, check for errors, and verify connections, ensuring all commands are functioning as expected. This process often involves checking monitored files and ensuring messages are transmitted correctly.
What is the best way to create a command for file monitoring?
Creating a command to monitor files involves using the following command structure in your script or directory. It’s crucial to specify parameters for the monitored files and to test the command with the same test across different paths. This way, you can verify if it’s effective in detecting changes or blocked access attempts.
How do I modify the username for a version update?
To modify the username for a version update in your script, specify the correct parameters in your script and execute the required commands. You can use a Python script to automate this process, ensuring that the settings are updated in your directory according to the new version guidelines.
What should I do if I detect an error during installation?
If an error is detected during installation, first check the wazuh documentation for the exact rule ID and error descriptions. Verify the connection and parameters used during installation. Follow the correct commands to resolve the error, and consider modifying your script if necessary. This helps ensure your installation and system operate smoothly.
What is the role of the Wazuh manager in system monitoring?
The Wazuh manager is a central component in system monitoring, responsible for handling data collection, analysis, and storage. It processes alerts from monitored files and identifies any inconsistencies or security events. By integrating with the wazuh dashboard, the Wazuh manager offers real-time insights and comprehensive control over system activities.
How can the Wazuh dashboard improve security management?
The Wazuh dashboard provides a user-friendly interface for viewing security events managed by the Wazuh manager. It allows users to visualize data, assess vulnerabilities, and track the status of alerts in real time. This integration ensures efficient oversight of potential threats and facilitates quick responses to detected issues.
Conclusion
Determining the exact number of endpoints Wazuh can handle depends on various factors, including system architecture, resource allocation, and specific use cases. While precise numerical limits are not explicitly stated in the available documentation, real-world implementations demonstrate Wazuh’s capability to scale effectively in diverse environments. By carefully planning and optimizing your deployment, Wazuh can serve as a robust and scalable security solution for your organization.