Cloud security is a growing priority for organizations leveraging Amazon Web Services (AWS). One of the most effective ways to monitor AWS activity logs and detect potential security threats is by integrating AWS CloudTrail with Wazuh, an open-source security monitoring platform.
Why is this integration important?
- AWS CloudTrail provides detailed audit logs of all API calls and user activity within an AWS environment.
- Wazuh helps analyze, correlate, and alert on security events, identifying potential threats in real time.
- Together, they create a proactive cloud security monitoring system, enhancing compliance and threat detection.
In this guide, we’ll explore:
How AWS CloudTrail and Wazuh work together
Step-by-step setup instructions
Best practices for cloud security monitoring
Real-world use cases and troubleshooting tips
Let’s dive into what AWS CloudTrail and Wazuh are, and why this integration is critical for cloud security.
What is AWS CloudTrail and Wazuh?
What is AWS CloudTrail?
AWS CloudTrail is a logging service that records API calls and events across an AWS environment. It helps organizations track user activity, resource changes, and potential security threats by maintaining a detailed audit trail.
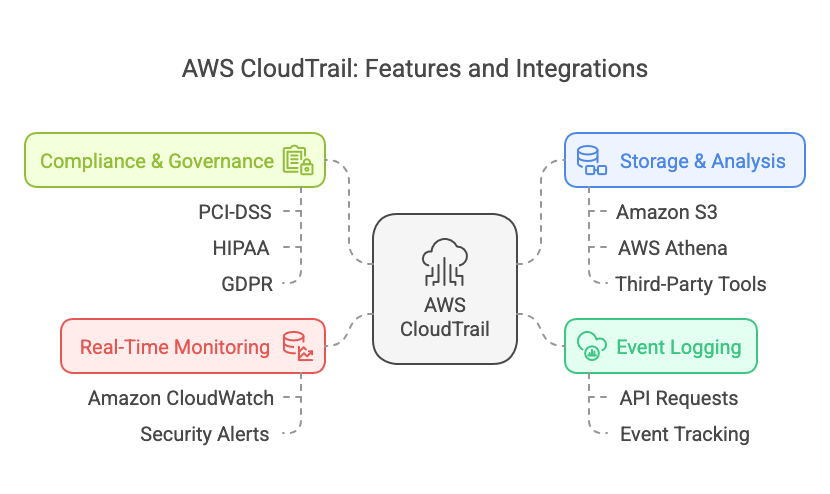
Key Features of AWS CloudTrail:
- Event Logging: Captures all API requests made to AWS services.
- Real-Time Monitoring: Works with Amazon CloudWatch to trigger security alerts.
- Compliance & Governance: Meets industry regulations such as PCI-DSS, HIPAA, and GDPR.
- Storage & Analysis: Stores logs in Amazon S3, which can be further analyzed with AWS Athena or third-party tools like Wazuh.
For more details on AWS CloudTrail, visit AWS CloudTrail Documentation.
What is Wazuh?
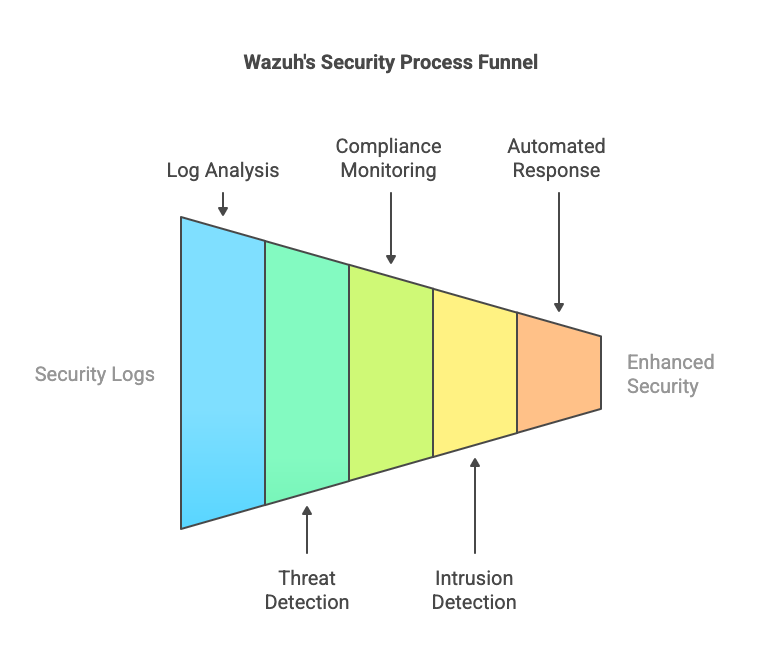
Wazuh is a free, open-source Security Information and Event Management (SIEM) solution designed to help organizations identify threats, ensure compliance, and respond to security incidents efficiently.
Key Features of Wazuh:
- Log Analysis & Threat Detection: Processes security logs from various sources, including AWS CloudTrail.
- Compliance Monitoring: Helps organizations meet security standards by detecting misconfigurations and unauthorized access.
- Intrusion Detection System (IDS): Uses rules-based and behavioral analytics to identify suspicious activity.
- Automated Alerts & Response: Can trigger alerts and automate security responses when suspicious behavior is detected.
Learn more about Wazuh from the official documentation.
How AWS CloudTrail and Wazuh Work Together
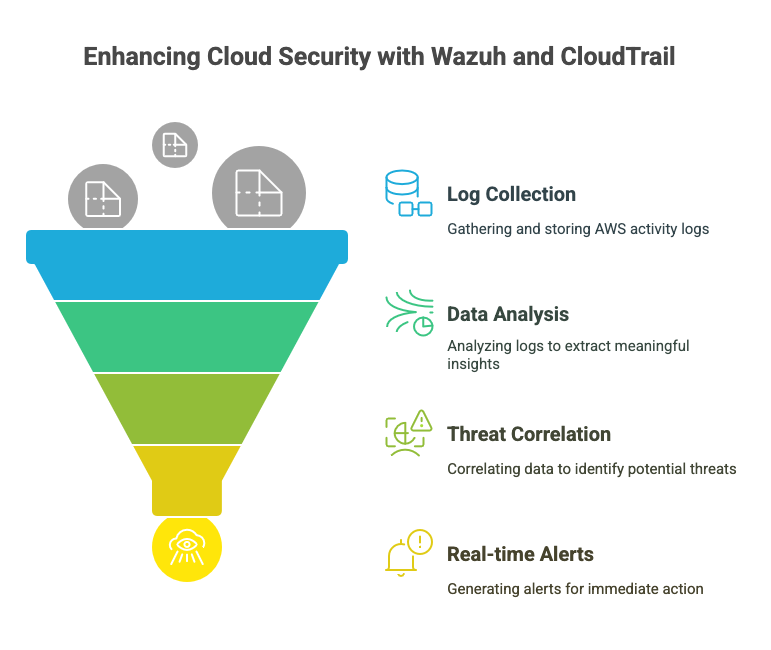
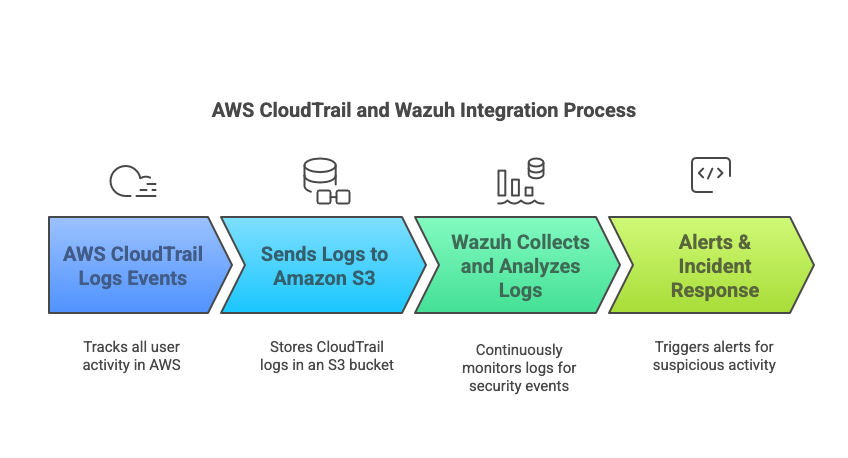
By integrating AWS CloudTrail with Wazuh, you can centralize cloud security monitoring and automate threat detection. Here’s how the integration works:
- AWS CloudTrail Logs Events → Tracks all user activity, including logins, API calls, and security group modifications.
- Sends Logs to Amazon S3 → Stores CloudTrail logs in an S3 bucket for long-term storage.
- Wazuh Collects and Analyzes Logs → Wazuh continuously monitors CloudTrail logs for security events.
- Alerts & Incident Response → Wazuh triggers alerts when it detects suspicious activity, helping security teams respond quickly.
Comparison Table: AWS CloudTrail vs. Wazuh
| Feature | AWS CloudTrail | Wazuh |
|---|---|---|
| Primary Function | Logs AWS activity | Analyzes and detects security threats |
| Data Storage | Amazon S3 | Wazuh Indexer or external SIEM |
| Threat Detection | No | Yes, with real-time alerts |
| Compliance Monitoring | Limited | Extensive |
| Integration with Other Tools | AWS-native services (e.g., CloudWatch) | Works with AWS, on-prem, and third-party logs |
| Automated Response | No | Yes, supports automated actions |
By combining AWS CloudTrail’s event logging with Wazuh’s security intelligence, organizations can create a powerful cloud security framework that detects unauthorized access, privilege escalations, and policy violations in real time.
Now, let’s move on to the step-by-step integration guide for setting up AWS CloudTrail with Wazuh. This section includes clear instructions, best practices, and a configuration table for reference.
How to Integrate AWS CloudTrail with Wazuh (Step-by-Step Guide)
Integrating AWS CloudTrail with Wazuh enables centralized security monitoring by collecting and analyzing AWS activity logs. Follow these steps to set up the integration.
Step 1: Enable AWS CloudTrail
Before Wazuh can analyze AWS logs, you need to enable AWS CloudTrail to capture events.
- Log in to AWS Console and go to CloudTrail.
- Click “Create Trail” and configure:
- Trail Name: wazuh-cloudtrail-logs
- Event Type: Select Management Events and Data Events (for deeper visibility).
- S3 Bucket: Create a new or select an existing Amazon S3 bucket where logs will be stored.
- Enable Log File Validation to ensure integrity.
- Click Create to activate CloudTrail.
💡 For best security practices, enable Multi-Region CloudTrail to monitor activity across all AWS regions.
Official AWS CloudTrail Setup Guide
Step 2: Set Up an S3 Bucket for Log Storage
- Go to the Amazon S3 Console.
- Click Create Bucket and name it something like wazuh-cloudtrail-logs.
- Enable Object Versioning to keep historical logs.
- Set Up Access Permissions:
- In the Bucket Policy, allow Wazuh to read CloudTrail logs:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": "*", "Action": "s3:GetObject", "Resource": "arn:aws:s3:::wazuh-cloudtrail-logs/*" } ] } - Click Create Bucket.
💡 For security, restrict S3 access using IAM roles instead of a wildcard * policy.
Step 3: Configure Wazuh to Collect AWS CloudTrail Logs
Now, configure Wazuh to collect logs from your AWS CloudTrail S3 bucket.
1. Install AWS Module in Wazuh
On your Wazuh Manager, install the AWS integration module:
apt install wazuh-integrations
2. Configure the AWS Module
Edit the Wazuh configuration file (/var/ossec/etc/ossec.conf) and add:
<wodle name="aws-s3"> <disabled>no</disabled> <interval>10m</interval> <run_on_start>yes</run_on_start> <bucket>wazuh-cloudtrail-logs</bucket> <aws_profile>default</aws_profile> <trail_name>wazuh-cloudtrail-logs</trail_name> <only_logs_after>7d</only_logs_after> </wodle>
💡 Set only_logs_after to 7 days to avoid processing old logs initially.
3. Restart Wazuh to Apply Changes
systemctl restart wazuh-manager
Step 4: Verify Wazuh is Receiving Logs
- Check Wazuh Logs to confirm CloudTrail events are being ingested:
tail -f /var/ossec/logs/ossec.log | grep aws
- View Events in Wazuh Dashboard:
- Log in to Wazuh Kibana (or OpenSearch Dashboard).
- Navigate to Security Events → Filter for aws.cloudtrail.
💡 If logs are missing, check IAM permissions and ensure the Wazuh AWS module is properly configured.
Step 5: Create Wazuh Alerts for AWS CloudTrail Events
Once logs are ingested, you can create custom alerts in Wazuh based on specific AWS activity.
Example: Alert for Unauthorized Access Attempts
- Open the Wazuh rules file:
nano /var/ossec/rules/local_rules.xml
- Add a custom rule to detect failed login attempts:
<group name="aws, cloudtrail, authentication"> <rule id="100001" level="10"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">ConsoleLogin</field> <field name="aws.cloudtrail.responseElements.ConsoleLogin">Failure</field> <description>Failed AWS Console Login Attempt</description> </rule> </group> - Save and restart Wazuh:
systemctl restart wazuh-manager
💡 You can create similar alerts for events like IAM role changes, S3 bucket modifications, and privilege escalations.
Comparison Table: CloudTrail & Wazuh Setup Components
| Component | AWS CloudTrail | Wazuh |
|---|---|---|
| Purpose | Logs AWS API activity | Analyzes and detects security threats |
| Log Storage | Amazon S3 | Wazuh Indexer (or external SIEM) |
| Threat Detection | No | Yes (custom alerts and rules) |
| Configuration | CloudTrail console + S3 bucket setup | Install AWS module & configure logs |
| Alerting | Uses AWS CloudWatch | Uses Wazuh rules & alerting engine |
Best Practices for AWS CloudTrail + Wazuh Integration
Enable Multi-Region CloudTrail → Ensures visibility across all AWS regions.
Restrict S3 Bucket Access → Use IAM roles instead of public access.
Regularly Review Wazuh Alerts → Adjust rules to reduce false positives.
Automate Incident Response → Use Wazuh to trigger automated security actions.
Now, let’s move on to Real-World Use Cases of Wazuh AWS CloudTrail Integration, showcasing how organizations leverage this integration to improve cloud security, compliance, and threat detection.
Real-World Use Cases of Wazuh AWS CloudTrail Integration
Integrating AWS CloudTrail with Wazuh provides a robust cloud security monitoring solution that helps organizations detect threats, investigate incidents, and enforce compliance. Here are real-world scenarios where this integration proves invaluable.
1. Detecting Unauthorized AWS Console Login Attempts
Use Case: A financial institution wants to monitor and block unauthorized AWS login attempts.
How It Works:
- CloudTrail logs AWS login events.
- Wazuh analyzes the logs and detects failed logins.
- An alert is triggered when repeated failed login attempts occur.
- The security team is notified in real time.
Example Wazuh Rule:
<rule id="100002" level="12"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">ConsoleLogin</field> <field name="aws.cloudtrail.responseElements.ConsoleLogin">Failure</field> <description>Multiple Failed AWS Console Logins Detected</description> </rule>
Impact:
Early detection of brute-force login attempts.
Faster response to potential account compromises.
Reduces false positives by filtering normal failed login patterns.
2. Monitoring IAM Role Changes for Privilege Escalation
Use Case: A SaaS company wants to detect suspicious privilege escalations in AWS.
How It Works:
- AWS CloudTrail logs all IAM role changes.
- Wazuh flags high-risk role modifications, such as:
- Adding users to the Administrator group.
- Modifying IAM role permissions.
- An alert is triggered if an unauthorized role modification is detected.
Example Wazuh Rule for IAM Privilege Escalation:
<rule id="100002" level="12"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">ConsoleLogin</field> <field name="aws.cloudtrail.responseElements.ConsoleLogin">Failure</field> <description>Multiple Failed AWS Console Logins Detected</description> </rule>
Impact:
Prevents privilege abuse by tracking IAM modifications.
Meets compliance standards like SOC 2, PCI-DSS, and HIPAA.
Reduces insider threats by identifying unauthorized privilege escalations.
3. Detecting Suspicious S3 Bucket Access
Use Case: A healthcare provider wants to monitor AWS S3 bucket activity for potential data leaks.
How It Works:
- CloudTrail logs all S3 API requests.
- Wazuh detects suspicious S3 actions, such as:
- Unusual “GetObject” requests.
- Public access modifications.
- Excessive data downloads.
- Security teams get an alert for abnormal activity.
Example Wazuh Rule for Unusual S3 Access:
<rule id="100004" level="15"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">GetObject</field> <field name="aws.cloudtrail.userIdentity.type">IAMUser</field> <field name="aws.cloudtrail.sourceIPAddress" type="regex">!^192\.168\.</field> <description>Unusual S3 Object Access from External IP</description> </rule>
Impact:
Prevents unauthorized access to sensitive healthcare records.
Identifies potential data leaks in real time.
Protects compliance with HIPAA, GDPR, and NIST 800-53.
4. Automated Response to Security Incidents
Use Case: An eCommerce company wants to automate threat response when Wazuh detects an anomaly.
How It Works:
- Wazuh identifies suspicious AWS activity.
- A custom script is executed to auto-remediate threats.
- Security teams receive alerts and logs via Slack or email.
Example: Wazuh Response Automation for AWS CloudTrail Events
<rule id="100005" level="13"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">AuthorizeSecurityGroupIngress</field> <description>Unauthorized Security Group Modification Detected</description> <mitigation_action>bash /var/ossec/scripts/disable_aws_key.sh</mitigation_action> </rule>
Impact:
Immediate containment of unauthorized network changes.
Faster incident response by automating remediation.
Reduces attack surface by enforcing security policies in real time.
5. Ensuring Compliance with AWS Security Policies
Use Case: A government agency needs to ensure continuous compliance monitoring.
How It Works:
- CloudTrail tracks AWS configuration changes.
- Wazuh validates compliance with industry standards.
- Non-compliant configurations trigger alerts.
Example Wazuh Rule for Compliance Monitoring:
<rule id="100006" level="10"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">PutBucketAcl</field> <field name="aws.cloudtrail.requestParameters.x-amz-acl">public-read</field> <description>S3 Bucket Public Access Detected - Compliance Risk</description> </rule>
Impact:
Automated compliance checks reduce audit effort.
Protects against security misconfigurations in AWS.
Reduces compliance violations before they become critical.
Summary Table: Real-World Use Cases for Wazuh & AWS CloudTrail
| Use Case | Wazuh Rule Example | Benefit |
|---|---|---|
| Detecting Unauthorized Logins | Failed AWS ConsoleLogin | Prevents brute-force attacks |
| IAM Privilege Escalation | AttachRolePolicy changes | Protects against privilege abuse |
| Suspicious S3 Access | Unusual GetObject requests | Detects potential data leaks |
| Automated Threat Response | Modify Security Groups | Auto-remediates unauthorized changes |
| Compliance Monitoring | S3 Public Access alerts | Ensures regulatory compliance |
Why This Integration is Essential for Cloud Security
By integrating AWS CloudTrail with Wazuh, organizations gain: Real-time threat detection with AI-powered alerts.
Automated response capabilities for faster security incident handling.
Stronger compliance posture with continuous monitoring.
Reduced risk of cloud misconfigurations that lead to breaches.
Want to learn more? Visit the Wazuh Cloud Security Documentation for additional insights.
FAQs About Wazuh AWS CloudTrail Integration
Below are answers to frequently asked questions about integrating AWS CloudTrail with Wazuh for cloud security monitoring.
What are the benefits of integrating AWS CloudTrail with Wazuh?
Integrating AWS CloudTrail with Wazuh offers multiple security and compliance benefits, including:
- Centralized Cloud Security Monitoring – Aggregates and analyzes AWS activity logs for security insights.
- Real-Time Threat Detection – Identifies unauthorized access, failed login attempts, and privilege escalations.
- Automated Incident Response – Triggers security alerts and scripts for auto-remediation.
- Regulatory Compliance – Helps organizations comply with standards like SOC 2, PCI-DSS, HIPAA, and GDPR.
Learn more about AWS security best practices.
Can Wazuh detect insider threats in AWS?
Yes! Wazuh monitors CloudTrail logs for signs of insider threats, such as:
- Unauthorized IAM role modifications
- Suspicious login attempts from internal IPs
- Unusual data access patterns in S3 buckets
- Excessive API requests to sensitive AWS services
By setting up custom Wazuh rules, organizations can flag and investigate insider threats before they escalate.
Does Wazuh support AWS CloudTrail multi-region tracking?
Yes, multi-region tracking is supported. To enable it:
- In AWS CloudTrail, enable “Multi-Region Trail” to collect logs from all AWS regions.
- Ensure the Wazuh configuration includes:
<trail_name>wazuh-cloudtrail-logs</trail_name>
- Verify Wazuh is receiving logs from multiple AWS regions using:
tail -f /var/ossec/logs/ossec.log | grep aws
💡 Multi-region tracking ensures threats aren’t missed across different AWS locations.
How do I create a Wazuh alert for failed AWS logins?
To detect failed AWS login attempts, add this custom rule in Wazuh:
<rule id="100007" level="12"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">ConsoleLogin</field> <field name="aws.cloudtrail.responseElements.ConsoleLogin">Failure</field> <description>Multiple Failed AWS Console Logins Detected</description> </rule>
💡 This helps identify potential brute-force attacks or unauthorized access attempts.
Can I visualize AWS CloudTrail logs in Wazuh’s dashboard?
Yes! Wazuh integrates with OpenSearch Dashboards (formerly Kibana) to provide a visual representation of AWS CloudTrail logs.
Steps to View AWS Logs in Wazuh Dashboard:
- Log in to Wazuh Dashboard.
- Navigate to Security Events → AWS CloudTrail.
- Apply filters to focus on IAM changes, S3 access, and login attempts.
Follow the Wazuh Dashboard Guide for a complete walkthrough.
What AWS services can Wazuh monitor besides CloudTrail?
In addition to AWS CloudTrail, Wazuh can collect security logs from:
- Amazon GuardDuty – Detects AWS threats using machine learning.
- AWS Config – Monitors AWS resource changes for compliance.
- Amazon S3 – Tracks storage access and potential data leaks.
- AWS VPC Flow Logs – Analyzes network activity and traffic patterns.
💡 Integrating multiple AWS security services enhances cloud threat intelligence.
How can I secure AWS CloudTrail logs from tampering?
To prevent unauthorized access or log tampering: Enable Log File Integrity Validation in CloudTrail.
Use Amazon S3 Bucket Policies to restrict access.
Encrypt Logs with AWS KMS (Key Management Service).
Regularly Monitor AWS IAM Permissions for suspicious changes.
Follow AWS’s log security recommendations for additional protection.
Can Wazuh trigger an automatic response to AWS security incidents?
Yes! Wazuh can trigger security scripts or notify teams via Slack, email, or SIEM integrations.
Example: Automatically Disable a Compromised AWS Key
To disable an AWS key if Wazuh detects unauthorized activity:
- Add a Wazuh mitigation script:
<mitigation_action>bash /var/ossec/scripts/disable_aws_key.sh</mitigation_action>
- Create a script /var/ossec/scripts/disable_aws_key.sh:
aws iam update-access-key --access-key-id $AWS_KEY_ID --status Inactive
- Restart Wazuh:
systemctl restart wazuh-manager
💡 This ensures fast incident response to AWS security threats.
What are the storage considerations for AWS CloudTrail logs in Wazuh?
Since CloudTrail logs can grow quickly, consider:
- S3 Lifecycle Policies – Automatically archive old logs to AWS Glacier.
- Log Rotation in Wazuh – Configure /var/ossec/logs/ to prevent storage overload.
- External SIEM Integration – Send logs to Splunk, ELK, or AWS Security Lake.
Read AWS’s best practices for log storage.
How much does it cost to integrate AWS CloudTrail with Wazuh?
The cost depends on: AWS CloudTrail pricing (per event) – Free for management events, paid for data events.
S3 storage – Depends on the size of logs stored.
Wazuh self-hosted or cloud – Free on self-hosted, costs for managed services.
💡 Use AWS Cost Explorer to estimate your CloudTrail logging expenses.
How does AWS Infrastructure support Wazuh agent operations?
AWS Infrastructure supports Wazuh agent operations by providing scalable cloud resources and tools necessary for monitoring and managing security across various environments. By integrating with AWS Management Console and other AWS services, Wazuh agents can effectively track AWS account activity and maintain comprehensive security logs, enabling auditing and effective incident response.
What are best practices for managing AWS account activity securely?
Best practices for managing AWS account activity securely include enabling auditing through CloudTrail, which helps log all account activities, ensuring compliance and security checks. Assign only the minimum permissions required by each user or service to follow the principle of least privilege, minimizing potential security risks. Regularly reviewing account activity-related controls can further enhance protection.
How can CloudTrail integration enhance AWS security configurations?
CloudTrail integration enhances AWS security configurations by providing detailed logs of account activity across AWS services. This allows monitoring for unauthorized changes or access, ensuring that only legitimate and intended actions occur. CloudTrail helps in identifying anomalies and supports compliance by maintaining reliable evidence of user activities, critical for auditing purposes.
Why is granting only the minimum permissions a key security strategy in AWS?
Granting only the minimum permissions necessary is a key security strategy in AWS because it reduces the potential attack surface by limiting access to resources. This approach ensures that users or services only have access to what is strictly needed for their roles, preventing accidental or malicious alterations to configurations and enhancing overall security within the infrastructure.
How does a Wazuh server benefit AWS user management?
A Wazuh server benefits AWS user management by providing enhanced security monitoring and log analysis capabilities. It enables the tracking of AWS user activities, integrating with the Amazon Web Services console to offer real-time insights into user operations. This functionality ensures prompt detection of anomalous behavior and aids in maintaining compliance with security policies.
What is the significance of using command line tools for AWS SDKs?
The significance of using command line tools for AWS SDKs lies in the ability to automate and streamline workflows directly within the AWS environment. These tools provide developers and administrators with powerful capabilities to manage AWS resources, implement user-related configurations, and automate repetitive tasks efficiently. The command line interface allows for greater flexibility and control within different configurations and development processes.
Why should account activity be retained and integrated with CloudTrail in AWS?
Retaining account activity and integrating it with CloudTrail in AWS is crucial for ensuring transparency and accountability within cloud environments. CloudTrail provides a detailed record of user and API activities, helping in tracking changes, detecting potential security breaches, and facilitating compliance audits. By retaining these logs, organizations can ensure swift incident investigation and maintain robust security postures.
How does ‘read only’ permissions improve AWS security strategy?
‘Read only’ permissions improve AWS security strategy by restricting users to view-only access, preventing any changes to the resources or configurations. This approach is useful for roles that require monitoring without altering settings, thereby mitigating risks of accidental configurations or unauthorized access to sensitive information. It’s an effective measure to safeguard critical AWS infrastructures while granting essential access.
Why is it important to retain AWS account activity related records?
Retaining AWS account activity related records is important for maintaining a comprehensive audit trail and ensuring accountability within your cloud environment. These records, often tracked through CloudTrail, are essential for monitoring user actions, identifying unauthorized access attempts, and providing useful information during security audits or incident investigations.
How does integrating CloudTrail enhance AWS security?
Integrating CloudTrail enhances AWS security by offering a detailed log of user and API activity within your AWS account. This logging capability helps track changes, monitor access to resources, and detect potential security incidents. By having a clear event history, organizations can quickly respond to anomalies and ensure compliance with security policies and regulations.
What is the role of a credentials file in AWS management?
A credentials file in AWS management stores user-specific authentication data required for accessing AWS services through command line tools or SDKs. This file contains sensitive information such as access keys and secret keys, making it crucial to protect and manage correctly. Ensuring its security helps prevent unauthorized access and maintain the confidentiality and integrity of your AWS environment.
Why should you configure ‘debug mode’ and what does it offer?
Configuring ‘debug mode’ can provide verbose logging and diagnostic details during development and troubleshooting in AWS environments. It offers insights into the execution flow and can reveal underlying issues by logging additional useful information. This helps developers identify and resolve errors more efficiently, ensuring that configurations and integrations function correctly.

Cloud security is a growing priority for organizations leveraging Amazon Web Services (AWS). One of the most effective ways to monitor AWS activity logs and detect potential security threats is by integrating AWS CloudTrail with Wazuh, an open-source security monitoring platform.
Why is this integration important?
- AWS CloudTrail provides detailed audit logs of all API calls and user activity within an AWS environment.
- Wazuh helps analyze, correlate, and alert on security events, identifying potential threats in real time.
- Together, they create a proactive cloud security monitoring system, enhancing compliance and threat detection.
In this guide, we’ll explore:
How AWS CloudTrail and Wazuh work together
Step-by-step setup instructions
Best practices for cloud security monitoring
Real-world use cases and troubleshooting tips
Let’s dive into what AWS CloudTrail and Wazuh are, and why this integration is critical for cloud security.
What is AWS CloudTrail and Wazuh?
What is AWS CloudTrail?
AWS CloudTrail is a logging service that records API calls and events across an AWS environment. It helps organizations track user activity, resource changes, and potential security threats by maintaining a detailed audit trail.
Key Features of AWS CloudTrail:
- Event Logging: Captures all API requests made to AWS services.
- Real-Time Monitoring: Works with Amazon CloudWatch to trigger security alerts.
- Compliance & Governance: Meets industry regulations such as PCI-DSS, HIPAA, and GDPR.
- Storage & Analysis: Stores logs in Amazon S3, which can be further analyzed with AWS Athena or third-party tools like Wazuh.
For more details on AWS CloudTrail, visit AWS CloudTrail Documentation.
What is Wazuh?
Wazuh is a free, open-source Security Information and Event Management (SIEM) solution designed to help organizations identify threats, ensure compliance, and respond to security incidents efficiently.
Key Features of Wazuh:
- Log Analysis & Threat Detection: Processes security logs from various sources, including AWS CloudTrail.
- Compliance Monitoring: Helps organizations meet security standards by detecting misconfigurations and unauthorized access.
- Intrusion Detection System (IDS): Uses rules-based and behavioral analytics to identify suspicious activity.
- Automated Alerts & Response: Can trigger alerts and automate security responses when suspicious behavior is detected.
Learn more about Wazuh from the official documentation.
How AWS CloudTrail and Wazuh Work Together
By integrating AWS CloudTrail with Wazuh, you can centralize cloud security monitoring and automate threat detection. Here’s how the integration works:
- AWS CloudTrail Logs Events → Tracks all user activity, including logins, API calls, and security group modifications.
- Sends Logs to Amazon S3 → Stores CloudTrail logs in an S3 bucket for long-term storage.
- Wazuh Collects and Analyzes Logs → Wazuh continuously monitors CloudTrail logs for security events.
- Alerts & Incident Response → Wazuh triggers alerts when it detects suspicious activity, helping security teams respond quickly.
Comparison Table: AWS CloudTrail vs. Wazuh
| Feature | AWS CloudTrail | Wazuh |
|---|---|---|
| Primary Function | Logs AWS activity | Analyzes and detects security threats |
| Data Storage | Amazon S3 | Wazuh Indexer or external SIEM |
| Threat Detection | No | Yes, with real-time alerts |
| Compliance Monitoring | Limited | Extensive |
| Integration with Other Tools | AWS-native services (e.g., CloudWatch) | Works with AWS, on-prem, and third-party logs |
| Automated Response | No | Yes, supports automated actions |
By combining AWS CloudTrail’s event logging with Wazuh’s security intelligence, organizations can create a powerful cloud security framework that detects unauthorized access, privilege escalations, and policy violations in real time.
Now, let’s move on to the step-by-step integration guide for setting up AWS CloudTrail with Wazuh. This section includes clear instructions, best practices, and a configuration table for reference.
How to Integrate AWS CloudTrail with Wazuh (Step-by-Step Guide)
Integrating AWS CloudTrail with Wazuh enables centralized security monitoring by collecting and analyzing AWS activity logs. Follow these steps to set up the integration.
Step 1: Enable AWS CloudTrail
Before Wazuh can analyze AWS logs, you need to enable AWS CloudTrail to capture events.
- Log in to AWS Console and go to CloudTrail.
- Click “Create Trail” and configure:
- Trail Name: wazuh-cloudtrail-logs
- Event Type: Select Management Events and Data Events (for deeper visibility).
- S3 Bucket: Create a new or select an existing Amazon S3 bucket where logs will be stored.
- Enable Log File Validation to ensure integrity.
- Click Create to activate CloudTrail.
💡 For best security practices, enable Multi-Region CloudTrail to monitor activity across all AWS regions.
Official AWS CloudTrail Setup Guide
Step 2: Set Up an S3 Bucket for Log Storage
- Go to the Amazon S3 Console.
- Click Create Bucket and name it something like wazuh-cloudtrail-logs.
- Enable Object Versioning to keep historical logs.
- Set Up Access Permissions:
- In the Bucket Policy, allow Wazuh to read CloudTrail logs:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": "*", "Action": "s3:GetObject", "Resource": "arn:aws:s3:::wazuh-cloudtrail-logs/*" } ] } - Click Create Bucket.
💡 For security, restrict S3 access using IAM roles instead of a wildcard * policy.
Step 3: Configure Wazuh to Collect AWS CloudTrail Logs
Now, configure Wazuh to collect logs from your AWS CloudTrail S3 bucket.
1. Install AWS Module in Wazuh
On your Wazuh Manager, install the AWS integration module:
apt install wazuh-integrations
2. Configure the AWS Module
Edit the Wazuh configuration file (/var/ossec/etc/ossec.conf) and add:
<wodle name="aws-s3"> <disabled>no</disabled> <interval>10m</interval> <run_on_start>yes</run_on_start> <bucket>wazuh-cloudtrail-logs</bucket> <aws_profile>default</aws_profile> <trail_name>wazuh-cloudtrail-logs</trail_name> <only_logs_after>7d</only_logs_after> </wodle>
💡 Set only_logs_after to 7 days to avoid processing old logs initially.
3. Restart Wazuh to Apply Changes
systemctl restart wazuh-manager
Step 4: Verify Wazuh is Receiving Logs
- Check Wazuh Logs to confirm CloudTrail events are being ingested:
tail -f /var/ossec/logs/ossec.log | grep aws
- View Events in Wazuh Dashboard:
- Log in to Wazuh Kibana (or OpenSearch Dashboard).
- Navigate to Security Events → Filter for aws.cloudtrail.
💡 If logs are missing, check IAM permissions and ensure the Wazuh AWS module is properly configured.
Step 5: Create Wazuh Alerts for AWS CloudTrail Events
Once logs are ingested, you can create custom alerts in Wazuh based on specific AWS activity.
Example: Alert for Unauthorized Access Attempts
- Open the Wazuh rules file:
nano /var/ossec/rules/local_rules.xml
- Add a custom rule to detect failed login attempts:
<group name="aws, cloudtrail, authentication"> <rule id="100001" level="10"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">ConsoleLogin</field> <field name="aws.cloudtrail.responseElements.ConsoleLogin">Failure</field> <description>Failed AWS Console Login Attempt</description> </rule> </group> - Save and restart Wazuh:
systemctl restart wazuh-manager
💡 You can create similar alerts for events like IAM role changes, S3 bucket modifications, and privilege escalations.
Comparison Table: CloudTrail & Wazuh Setup Components
| Component | AWS CloudTrail | Wazuh |
|---|---|---|
| Purpose | Logs AWS API activity | Analyzes and detects security threats |
| Log Storage | Amazon S3 | Wazuh Indexer (or external SIEM) |
| Threat Detection | No | Yes (custom alerts and rules) |
| Configuration | CloudTrail console + S3 bucket setup | Install AWS module & configure logs |
| Alerting | Uses AWS CloudWatch | Uses Wazuh rules & alerting engine |
Best Practices for AWS CloudTrail + Wazuh Integration
Enable Multi-Region CloudTrail → Ensures visibility across all AWS regions.
Restrict S3 Bucket Access → Use IAM roles instead of public access.
Regularly Review Wazuh Alerts → Adjust rules to reduce false positives.
Automate Incident Response → Use Wazuh to trigger automated security actions.
Now, let’s move on to Real-World Use Cases of Wazuh AWS CloudTrail Integration, showcasing how organizations leverage this integration to improve cloud security, compliance, and threat detection.
Real-World Use Cases of Wazuh AWS CloudTrail Integration
Integrating AWS CloudTrail with Wazuh provides a robust cloud security monitoring solution that helps organizations detect threats, investigate incidents, and enforce compliance. Here are real-world scenarios where this integration proves invaluable.
1. Detecting Unauthorized AWS Console Login Attempts
Use Case: A financial institution wants to monitor and block unauthorized AWS login attempts.
How It Works:
- CloudTrail logs AWS login events.
- Wazuh analyzes the logs and detects failed logins.
- An alert is triggered when repeated failed login attempts occur.
- The security team is notified in real time.
Example Wazuh Rule:
<rule id="100002" level="12"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">ConsoleLogin</field> <field name="aws.cloudtrail.responseElements.ConsoleLogin">Failure</field> <description>Multiple Failed AWS Console Logins Detected</description> </rule>
Impact:
Early detection of brute-force login attempts.
Faster response to potential account compromises.
Reduces false positives by filtering normal failed login patterns.
2. Monitoring IAM Role Changes for Privilege Escalation
Use Case: A SaaS company wants to detect suspicious privilege escalations in AWS.
How It Works:
- AWS CloudTrail logs all IAM role changes.
- Wazuh flags high-risk role modifications, such as:
- Adding users to the Administrator group.
- Modifying IAM role permissions.
- An alert is triggered if an unauthorized role modification is detected.
Example Wazuh Rule for IAM Privilege Escalation:
<rule id="100002" level="12"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">ConsoleLogin</field> <field name="aws.cloudtrail.responseElements.ConsoleLogin">Failure</field> <description>Multiple Failed AWS Console Logins Detected</description> </rule>
Impact:
Prevents privilege abuse by tracking IAM modifications.
Meets compliance standards like SOC 2, PCI-DSS, and HIPAA.
Reduces insider threats by identifying unauthorized privilege escalations.
3. Detecting Suspicious S3 Bucket Access
Use Case: A healthcare provider wants to monitor AWS S3 bucket activity for potential data leaks.
How It Works:
- CloudTrail logs all S3 API requests.
- Wazuh detects suspicious S3 actions, such as:
- Unusual “GetObject” requests.
- Public access modifications.
- Excessive data downloads.
- Security teams get an alert for abnormal activity.
Example Wazuh Rule for Unusual S3 Access:
<rule id="100004" level="15"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">GetObject</field> <field name="aws.cloudtrail.userIdentity.type">IAMUser</field> <field name="aws.cloudtrail.sourceIPAddress" type="regex">!^192\.168\.</field> <description>Unusual S3 Object Access from External IP</description> </rule>
Impact:
Prevents unauthorized access to sensitive healthcare records.
Identifies potential data leaks in real time.
Protects compliance with HIPAA, GDPR, and NIST 800-53.
4. Automated Response to Security Incidents
Use Case: An eCommerce company wants to automate threat response when Wazuh detects an anomaly.
How It Works:
- Wazuh identifies suspicious AWS activity.
- A custom script is executed to auto-remediate threats.
- Security teams receive alerts and logs via Slack or email.
Example: Wazuh Response Automation for AWS CloudTrail Events
<rule id="100005" level="13"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">AuthorizeSecurityGroupIngress</field> <description>Unauthorized Security Group Modification Detected</description> <mitigation_action>bash /var/ossec/scripts/disable_aws_key.sh</mitigation_action> </rule>
Impact:
Immediate containment of unauthorized network changes.
Faster incident response by automating remediation.
Reduces attack surface by enforcing security policies in real time.
5. Ensuring Compliance with AWS Security Policies
Use Case: A government agency needs to ensure continuous compliance monitoring.
How It Works:
- CloudTrail tracks AWS configuration changes.
- Wazuh validates compliance with industry standards.
- Non-compliant configurations trigger alerts.
Example Wazuh Rule for Compliance Monitoring:
<rule id="100006" level="10"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">PutBucketAcl</field> <field name="aws.cloudtrail.requestParameters.x-amz-acl">public-read</field> <description>S3 Bucket Public Access Detected - Compliance Risk</description> </rule>
Impact:
Automated compliance checks reduce audit effort.
Protects against security misconfigurations in AWS.
Reduces compliance violations before they become critical.
Summary Table: Real-World Use Cases for Wazuh & AWS CloudTrail
| Use Case | Wazuh Rule Example | Benefit |
|---|---|---|
| Detecting Unauthorized Logins | Failed AWS ConsoleLogin | Prevents brute-force attacks |
| IAM Privilege Escalation | AttachRolePolicy changes | Protects against privilege abuse |
| Suspicious S3 Access | Unusual GetObject requests | Detects potential data leaks |
| Automated Threat Response | Modify Security Groups | Auto-remediates unauthorized changes |
| Compliance Monitoring | S3 Public Access alerts | Ensures regulatory compliance |
Why This Integration is Essential for Cloud Security
By integrating AWS CloudTrail with Wazuh, organizations gain: Real-time threat detection with AI-powered alerts.
Automated response capabilities for faster security incident handling.
Stronger compliance posture with continuous monitoring.
Reduced risk of cloud misconfigurations that lead to breaches.
Want to learn more? Visit the Wazuh Cloud Security Documentation for additional insights.
FAQs About Wazuh AWS CloudTrail Integration
Below are answers to frequently asked questions about integrating AWS CloudTrail with Wazuh for cloud security monitoring.
What are the benefits of integrating AWS CloudTrail with Wazuh?
Integrating AWS CloudTrail with Wazuh offers multiple security and compliance benefits, including:
- Centralized Cloud Security Monitoring – Aggregates and analyzes AWS activity logs for security insights.
- Real-Time Threat Detection – Identifies unauthorized access, failed login attempts, and privilege escalations.
- Automated Incident Response – Triggers security alerts and scripts for auto-remediation.
- Regulatory Compliance – Helps organizations comply with standards like SOC 2, PCI-DSS, HIPAA, and GDPR.
Learn more about AWS security best practices.
Can Wazuh detect insider threats in AWS?
Yes! Wazuh monitors CloudTrail logs for signs of insider threats, such as:
- Unauthorized IAM role modifications
- Suspicious login attempts from internal IPs
- Unusual data access patterns in S3 buckets
- Excessive API requests to sensitive AWS services
By setting up custom Wazuh rules, organizations can flag and investigate insider threats before they escalate.
Does Wazuh support AWS CloudTrail multi-region tracking?
Yes, multi-region tracking is supported. To enable it:
- In AWS CloudTrail, enable “Multi-Region Trail” to collect logs from all AWS regions.
- Ensure the Wazuh configuration includes:
<trail_name>wazuh-cloudtrail-logs</trail_name>
- Verify Wazuh is receiving logs from multiple AWS regions using:
tail -f /var/ossec/logs/ossec.log | grep aws
💡 Multi-region tracking ensures threats aren’t missed across different AWS locations.
How do I create a Wazuh alert for failed AWS logins?
To detect failed AWS login attempts, add this custom rule in Wazuh:
<rule id="100007" level="12"> <decoded_as>json</decoded_as> <field name="aws.cloudtrail.eventName">ConsoleLogin</field> <field name="aws.cloudtrail.responseElements.ConsoleLogin">Failure</field> <description>Multiple Failed AWS Console Logins Detected</description> </rule>
💡 This helps identify potential brute-force attacks or unauthorized access attempts.
Can I visualize AWS CloudTrail logs in Wazuh’s dashboard?
Yes! Wazuh integrates with OpenSearch Dashboards (formerly Kibana) to provide a visual representation of AWS CloudTrail logs.
Steps to View AWS Logs in Wazuh Dashboard:
- Log in to Wazuh Dashboard.
- Navigate to Security Events → AWS CloudTrail.
- Apply filters to focus on IAM changes, S3 access, and login attempts.
Follow the Wazuh Dashboard Guide for a complete walkthrough.
What AWS services can Wazuh monitor besides CloudTrail?
In addition to AWS CloudTrail, Wazuh can collect security logs from:
- Amazon GuardDuty – Detects AWS threats using machine learning.
- AWS Config – Monitors AWS resource changes for compliance.
- Amazon S3 – Tracks storage access and potential data leaks.
- AWS VPC Flow Logs – Analyzes network activity and traffic patterns.
💡 Integrating multiple AWS security services enhances cloud threat intelligence.
How can I secure AWS CloudTrail logs from tampering?
To prevent unauthorized access or log tampering: Enable Log File Integrity Validation in CloudTrail.
Use Amazon S3 Bucket Policies to restrict access.
Encrypt Logs with AWS KMS (Key Management Service).
Regularly Monitor AWS IAM Permissions for suspicious changes.
Follow AWS’s log security recommendations for additional protection.
Can Wazuh trigger an automatic response to AWS security incidents?
Yes! Wazuh can trigger security scripts or notify teams via Slack, email, or SIEM integrations.
Example: Automatically Disable a Compromised AWS Key
To disable an AWS key if Wazuh detects unauthorized activity:
- Add a Wazuh mitigation script:
<mitigation_action>bash /var/ossec/scripts/disable_aws_key.sh</mitigation_action>
- Create a script /var/ossec/scripts/disable_aws_key.sh:
aws iam update-access-key --access-key-id $AWS_KEY_ID --status Inactive
- Restart Wazuh:
systemctl restart wazuh-manager
💡 This ensures fast incident response to AWS security threats.
What are the storage considerations for AWS CloudTrail logs in Wazuh?
Since CloudTrail logs can grow quickly, consider:
- S3 Lifecycle Policies – Automatically archive old logs to AWS Glacier.
- Log Rotation in Wazuh – Configure /var/ossec/logs/ to prevent storage overload.
- External SIEM Integration – Send logs to Splunk, ELK, or AWS Security Lake.
Read AWS’s best practices for log storage.
How much does it cost to integrate AWS CloudTrail with Wazuh?
The cost depends on: AWS CloudTrail pricing (per event) – Free for management events, paid for data events.
S3 storage – Depends on the size of logs stored.
Wazuh self-hosted or cloud – Free on self-hosted, costs for managed services.
💡 Use AWS Cost Explorer to estimate your CloudTrail logging expenses.
How does AWS Infrastructure support Wazuh agent operations?
AWS Infrastructure supports Wazuh agent operations by providing scalable cloud resources and tools necessary for monitoring and managing security across various environments. By integrating with AWS Management Console and other AWS services, Wazuh agents can effectively track AWS account activity and maintain comprehensive security logs, enabling auditing and effective incident response.
What are best practices for managing AWS account activity securely?
Best practices for managing AWS account activity securely include enabling auditing through CloudTrail, which helps log all account activities, ensuring compliance and security checks. Assign only the minimum permissions required by each user or service to follow the principle of least privilege, minimizing potential security risks. Regularly reviewing account activity-related controls can further enhance protection.
How can CloudTrail integration enhance AWS security configurations?
CloudTrail integration enhances AWS security configurations by providing detailed logs of account activity across AWS services. This allows monitoring for unauthorized changes or access, ensuring that only legitimate and intended actions occur. CloudTrail helps in identifying anomalies and supports compliance by maintaining reliable evidence of user activities, critical for auditing purposes.
Why is granting only the minimum permissions a key security strategy in AWS?
Granting only the minimum permissions necessary is a key security strategy in AWS because it reduces the potential attack surface by limiting access to resources. This approach ensures that users or services only have access to what is strictly needed for their roles, preventing accidental or malicious alterations to configurations and enhancing overall security within the infrastructure.
How does a Wazuh server benefit AWS user management?
A Wazuh server benefits AWS user management by providing enhanced security monitoring and log analysis capabilities. It enables the tracking of AWS user activities, integrating with the Amazon Web Services console to offer real-time insights into user operations. This functionality ensures prompt detection of anomalous behavior and aids in maintaining compliance with security policies.
What is the significance of using command line tools for AWS SDKs?
The significance of using command line tools for AWS SDKs lies in the ability to automate and streamline workflows directly within the AWS environment. These tools provide developers and administrators with powerful capabilities to manage AWS resources, implement user-related configurations, and automate repetitive tasks efficiently. The command line interface allows for greater flexibility and control within different configurations and development processes.
Why should account activity be retained and integrated with CloudTrail in AWS?
Retaining account activity and integrating it with CloudTrail in AWS is crucial for ensuring transparency and accountability within cloud environments. CloudTrail provides a detailed record of user and API activities, helping in tracking changes, detecting potential security breaches, and facilitating compliance audits. By retaining these logs, organizations can ensure swift incident investigation and maintain robust security postures.
How does ‘read only’ permissions improve AWS security strategy?
‘Read only’ permissions improve AWS security strategy by restricting users to view-only access, preventing any changes to the resources or configurations. This approach is useful for roles that require monitoring without altering settings, thereby mitigating risks of accidental configurations or unauthorized access to sensitive information. It’s an effective measure to safeguard critical AWS infrastructures while granting essential access.
Why is it important to retain AWS account activity related records?
Retaining AWS account activity related records is important for maintaining a comprehensive audit trail and ensuring accountability within your cloud environment. These records, often tracked through CloudTrail, are essential for monitoring user actions, identifying unauthorized access attempts, and providing useful information during security audits or incident investigations.
How does integrating CloudTrail enhance AWS security?
Integrating CloudTrail enhances AWS security by offering a detailed log of user and API activity within your AWS account. This logging capability helps track changes, monitor access to resources, and detect potential security incidents. By having a clear event history, organizations can quickly respond to anomalies and ensure compliance with security policies and regulations.
What is the role of a credentials file in AWS management?
A credentials file in AWS management stores user-specific authentication data required for accessing AWS services through command line tools or SDKs. This file contains sensitive information such as access keys and secret keys, making it crucial to protect and manage correctly. Ensuring its security helps prevent unauthorized access and maintain the confidentiality and integrity of your AWS environment.
Why should you configure ‘debug mode’ and what does it offer?
Configuring ‘debug mode’ can provide verbose logging and diagnostic details during development and troubleshooting in AWS environments. It offers insights into the execution flow and can reveal underlying issues by logging additional useful information. This helps developers identify and resolve errors more efficiently, ensuring that configurations and integrations function correctly.